· deepdives · 7 min read
Breaking Down COOP and COEP: Common Misconceptions and Controversies
A practical, myth-busting guide to Cross-Origin-Opener-Policy (COOP) and Cross-Origin-Embedder-Policy (COEP): what they do, why teams argue about them, how to adopt them without breaking your site, and when they actually matter.

Outcome-first: By the end of this article you’ll be able to decide whether COOP+COEP are right for your site, spot the real causes of common breakage, and implement a safe rollout plan that avoids surprising outages.
Quick orientation - what these headers do (in plain terms)
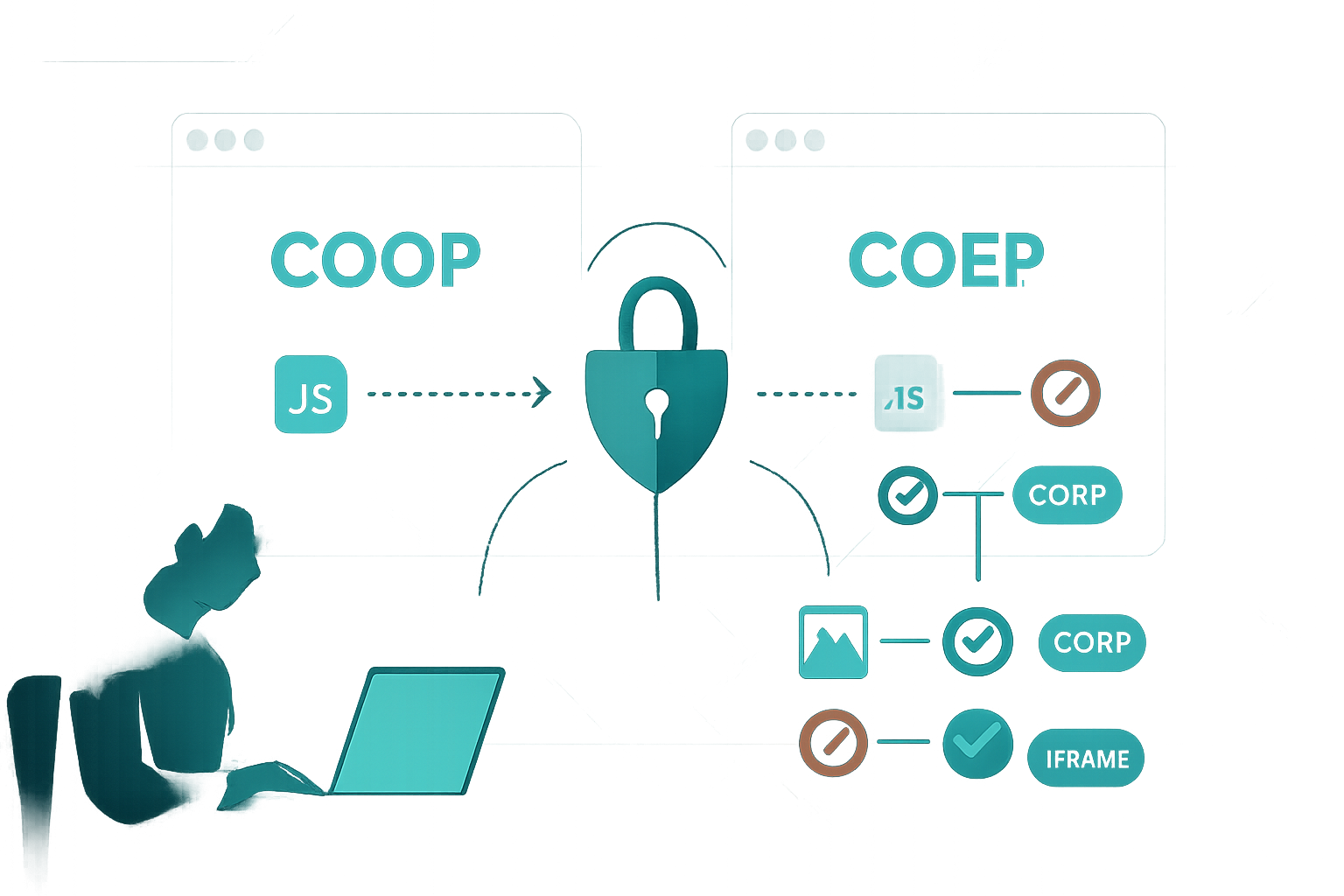
- Cross-Origin-Opener-Policy (COOP) controls whether your top-level page shares a browsing context group with cross-origin pages. In practice it isolates the top-level page from other origins’ windows and tabs. See MDN for the exact header values and semantics: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Opener-Policy
- Cross-Origin-Embedder-Policy (COEP) forces embedded cross-origin resources (images, scripts, iframes, etc.) to be explicitly loadable by CORS or to opt into being shared using appropriate resource headers (e.g., CORP or CORS). MDN has a good explainer: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Embedder-Policy
Together (COOP: same-origin + COEP: require-corp), they create a cross-origin isolated browsing environment. That isolation unlocks powerful capabilities (notably re-enabling SharedArrayBuffer and other high-resolution primitives) and reduces certain classes of cross-origin information leaks. A readable deep-dive with motivation and history is on web.dev: https://web.dev/coop-coep/.
The most common misconceptions (and the truth)
- “COOP/COEP are only about security, so they must only ever be good.”
- Partly true, partly misleading. They do improve isolation and enable features that were disabled for security reasons (e.g., restoring SharedArrayBuffer after Spectre mitigations). But applying them changes how your site integrates third-party content. That creates functional trade-offs, not just security wins.
- “If I add COOP+COEP they will immediately break everything that’s third-party - analytics, ads, embeds, etc.”
- Not always. They can break resources that aren’t served with the right CORS/CORP semantics, but most popular vendors now provide CORS-compatible endpoints. Problems occur when you rely on older or non-CORS-friendly third-party scripts or opaque resources.
- “COOP kills popups and window.opener functionality for good.”
- Not quite.
Cross-Origin-Opener-Policy: same-originsevers window relationships for security, but there is a compromise valuesame-origin-allow-popupsthat preserves opener links for windows your site explicitly opens (useful for OAuth flows and payment popups). See MDN for header values: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Opener-Policy
- “COEP is the same as CORS.”
- No. CORS is a mechanism that allows cross-origin requests with explicit server permission. COEP enforces that any embedded cross-origin resource must either be COOP/COEP/CORS-compliant (or include CORP/CORS headers). It’s policy enforcement at the document level to require explicit consent rather than lax, implicit embedding.
- “COOP+COEP are only for tiny experimental sites who need SharedArrayBuffer.”
- Not only. They’re necessary for certain Web Platform features, but also provide long-term security hardening and predictable isolation behavior. That can be valuable for large applications, particularly those that use cross-window messaging, WebAssembly, or high-precision timers.
Common controversies and the real trade-offs
- Complexity vs. benefit
Critic: “These headers add complexity and few teams reap the benefits.”
Counterpoint: They do add complexity where you must audit resource supply chains and fix a handful of resources. But the complexity is concentrated - a small number of third-party endpoints usually cause the majority of breakage. If you need the capabilities (e.g., SharedArrayBuffer for high-performance multi-threaded WebAssembly), the cost is clearly worth it. If you don’t, there’s no urgent need to adopt immediately.
- Third-party breakage and the ad/analytics ecosystem
Critic: “Ads and analytics won’t work, hurting revenue and measurement.”
Counterpoint: Many modern vendors have CORS-friendly versions. For those who don’t, tactics exist: use server-side collection/proxying, migrate to vendors who support CORP/CORS, or load third-party content in an isolated iframe that intentionally doesn’t inherit COOP/COEP (with appropriate sandboxing). This is a migration challenge, not an impossible technical barrier.
- Browser inconsistency and rollout pain
Critic: “Browsers handle these headers differently and debugging is a nightmare.”
Counterpoint: Browser support for COOP/COEP is relatively mature across Chromium and Firefox. Use staging, the report-only headers, and the console messages to detect failures before they hit users. The initial detection/debugging is the hard part; once you identify offending resources the fixes are straightforward.
- Privacy/fingerprinting concerns
Critic: “Isolating contexts changes the fingerprint surface and could harm privacy.”
Counterpoint: COOP/COEP’s intent is to reduce cross-origin leakage. Some privacy researchers worry about fingerprinting surface changes - but those concerns are orthogonal to the core trade-off: either you isolate to reduce shared state and timing leaks or you remain lax and keep those vectors open. The privacy argument is nuanced, but isolation generally helps mitigate certain cross-site attack vectors.
Practical rollout: a checklist to avoid breaking the site
- Audit: list every third-party resource embedded on pages you plan to isolate (scripts, images, iframes, fonts, etc.).
- Test environment: enable COOP/COEP on a staging domain. Don’t enable in production until you’ve resolved the warnings.
- Use report-only headers to gather clues (where available). Example headers to test:
Cross-Origin-Opener-Policy-Report-Only: same-origin; report-to="my-coop-group"
Cross-Origin-Embedder-Policy-Report-Only: require-corp; report-to="my-coep-group"(Implement reporting endpoints using the Reporting API to collect violation reports.) 4. Fix one resource class at a time:
- Scripts and fonts: ask vendors to serve with CORS (Access-Control-Allow-Origin) or host them on your domain.
- Images/ifames: add CORP (Cross-Origin-Resource-Policy) headers on those resources or serve them with CORS.
- Analytics: migrate to CORS-enabled endpoints or do server-side proxying/collection.
- Use
crossoriginattributes where appropriate:<script crossorigin="anonymous" src="..."></script>to request CORS-enabled script resources. - For popups/OAuth: prefer
same-origin-allow-popupsif you need opener relationships for windows you open. - Measure: verify functionality and performance with real-world pages and user journeys.
- Roll out gradually and have a rollback plan.
Example server headers (Nginx):
add_header Cross-Origin-Opener-Policy "same-origin";
add_header Cross-Origin-Embedder-Policy "require-corp";Express (Node.js) example middleware:
app.use((req, res, next) => {
res.setHeader('Cross-Origin-Opener-Policy', 'same-origin');
res.setHeader('Cross-Origin-Embedder-Policy', 'require-corp');
next();
});What breaks and how to fix it (practical patterns)
- Broken third-party script: request vendor support for CORS or host the library yourself under your origin.
- Broken image/font: add
Cross-Origin-Resource-Policy: cross-originorsame-siteas appropriate on the resource, or serve it with CORS. - Embedded iframe from an old partner: put that content in a sandboxed iframe on a separate origin and communicate via postMessage.
- Ads that cannot be CORS-enabled: either keep ad slots on non-isolated pages or use an isolated iframe approach for the rest of your app.
Useful reference: Cross-Origin-Resource-Policy (CORP) doc on MDN: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Resource-Policy
When to adopt COOP+COEP - decision guide
Adopt COOP+COEP if any of the following apply:
- You need SharedArrayBuffer or other high-precision features.
- You run a single-page app or web app where cross-origin leaks are a realistic threat and you want predictable isolation.
- You control most of the embedded resources or are ready to migrate vendors.
Delay adoption if:
- Your app depends heavily on legacy third-party widgets or ad vendors who can’t be migrated.
- You don’t need cross-origin-isolated features and the migration cost outweighs the benefits.
Counterarguments to common critics (short and sharp)
- “It’s overkill for regular websites.” - If you don’t need the features or security gains, don’t deploy. This is a tool, not a mandate.
- “It’ll destroy the ad ecosystem.” - It changes the ecosystem. Vendors evolve; some already support CORS/CORP. The short-term migration is a cost, but long-term it forces clearer, safer integrations.
- “It’s too brittle.” - Proper testing, staging, and using report-only modes make adoption predictable. Breakage is real but solvable.
Final verdict - practical, not dogmatic
COOP and COEP are powerful and sometimes controversial because they change assumed browser behaviors that many sites rely on. They are not a silver bullet and adopting them without preparation will cause outages. But when a team needs the capabilities they enable - or wants to harden an app against cross-origin leakage - the benefits are substantial. The correct approach is pragmatic: audit, test, fix the small set of incompatible resources, and roll out gradually. Don’t adopt because it’s fashionable; adopt when the feature set or security posture justifies the migration effort. Do the work once, and your app becomes safer and better defined.
Further reading and references
- MDN: Cross-Origin-Opener-Policy - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Opener-Policy
- MDN: Cross-Origin-Embedder-Policy - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Embedder-Policy
- web.dev: COOP and COEP explainer - https://web.dev/coop-coep/
- MDN: Cross-Origin-Resource-Policy (CORP) - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Resource-Policy