· deepdives · 6 min read
Understanding COOP and COEP: The Future of Secure Data Sharing
Learn how Cross-Origin-Opener-Policy (COOP) and Cross-Origin-Embedder-Policy (COEP) work, why they matter for modern web security and powerful browser features, and how to implement them safely-step by step with examples, nginx/Express/Apache snippets, and a migration checklist.
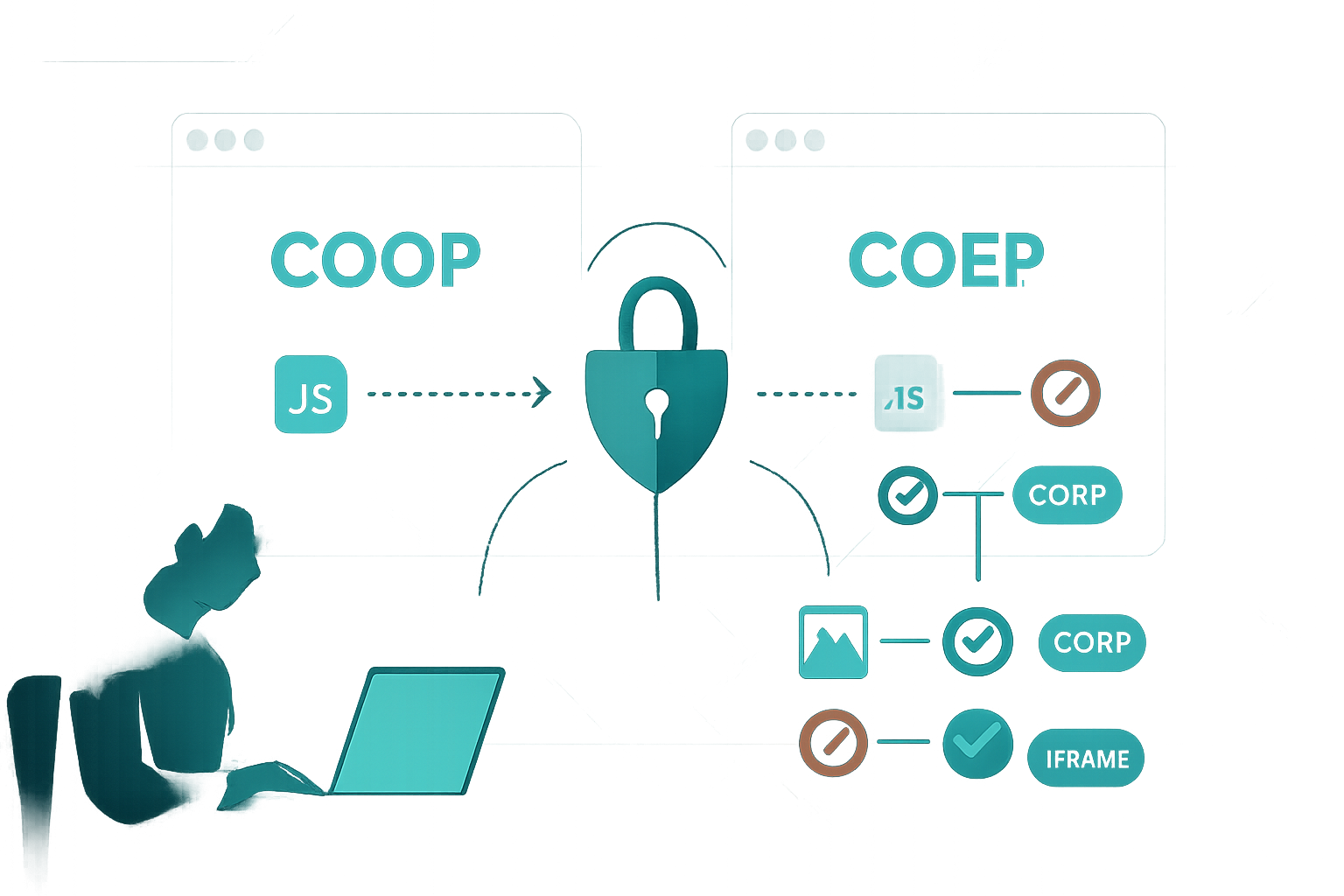
Introduction - what you’ll be able to do
By the end of this article you’ll be able to protect top-level pages from opener-based attacks, create cross-origin isolated pages, and unlock powerful browser features (like SharedArrayBuffer and high-resolution timers) without unexpected breakage. Short explanation first: use COOP and COEP together to create a secure, cross-origin isolated environment; then learn how to roll them out safely and fix common roadblocks.
Why COOP and COEP matter (the outcome)
- They harden web pages against modern cross-origin attack vectors (Spectre-like side channels and opener-based tampering).
- They let you enable high-performance and security-sensitive APIs that require cross-origin isolation (for example, SharedArrayBuffer, performance.measureMemory, and some high-resolution timing APIs).
- They change how resources from other origins are allowed to interact with your page. That can break third-party scripts and embeds if you don’t plan for it-but it also forces you to think intentionally about resource trust.
In short: safer pages, new capabilities, and an operational cost to migrate third-party content. The payoff is real. Powerful features require isolation. And isolation starts with COOP and COEP.
What are COOP and COEP? Quick definitions
Cross-Origin-Opener-Policy (COOP) controls whether a top-level document shares a Browsing Context Group with cross-origin documents. It prevents other origins from accessing window.opener and related shared resources when set to isolate.
- Header:
Cross-Origin-Opener-Policy - Common values:
same-origin,same-origin-allow-popups,unsafe-none(default). - Docs: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Opener-Policy
- Header:
Cross-Origin-Embedder-Policy (COEP) controls whether a document can load cross-origin resources that do not explicitly opt in to being embedded.
- Header:
Cross-Origin-Embedder-Policy - Common values:
require-corp,unsafe-none(default). - Docs: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Embedder-Policy
- Header:
Cross-Origin-Resource-Policy (CORP) is a resource-side header used to opt a resource into allowing cross-origin embedding.
- Header:
Cross-Origin-Resource-Policy - Values:
same-origin,same-site,cross-origin. - Docs: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Resource-Policy
- Header:
Use COOP + COEP together to produce a cross-origin isolated page.
How they work together - the mechanics (plain language)
- COOP isolates the top-level page from other origins by ensuring it does not share the same Browsing Context Group with cross-origin pages. This removes DOM-level access vectors (e.g., window.opener) between those contexts.
- COEP enforces that every resource your page embeds (scripts, images, iframes, fonts, workers, etc.) must either be same-origin or explicitly opt in via CORP.
- When both are in place, the user agent gives the page cross-origin isolation status. That status is the prerequisite for sensitive browser features that expose coarse-grained timing or shared memory.
Important nuance: COEP (require-corp) does not consider ordinary CORS approval sufficient. A resource must explicitly opt in using CORP or be same-origin. If a third-party resource does not serve a compatible CORP header, the browser will refuse to load it when COEP is enabled. For more background: see Google’s guide on cross-origin isolation: https://web.dev/coop-coep/ and MDN linked above.
Values and what they mean (concise)
COOP:
unsafe-none- default, no isolation.same-origin- isolate; other origins cannot share browsing context; blocks opener cross-origin access.same-origin-allow-popups- isolate but allow popups opened by your page to keep an opener relationship (useful if you need popup communication).
COEP:
unsafe-none- default, no embedder checks.require-corp- only load resources that are same-origin or provide an explicit CORP header allowing embedding.
CORP (resource-side):
same-origin,same-site, orcross-origin.
Real-world implications (what breaks)
When you enable COEP/COOP, expect:
- Third-party scripts, analytics, ads, CDNs, fonts, or images that do not send CORP may be blocked.
- Embedded cross-origin iframes or workers may fail to load unless they opt in.
- Cookies and CORS behavior are not directly changed by COEP/COOP; the failures you see are resource-embed policy failures, not CORS errors.
That’s why migration planning is essential.
Practical implementation examples
Recommendation: Start with the Report-Only headers to discover breakage before enforcing.
- Report-only headers (safe to deploy in production to detect breakage):
Cross-Origin-Opener-Policy-Report-Only: same-origin
Cross-Origin-Embedder-Policy-Report-Only: require-corp- Enforce headers (when ready):
Cross-Origin-Opener-Policy: same-origin
Cross-Origin-Embedder-Policy: require-corpnginx
# Add to your server block
add_header Cross-Origin-Opener-Policy "same-origin";
add_header Cross-Origin-Embedder-Policy "require-corp";Apache
# In your site config or .htaccess (with mod_headers)
Header set Cross-Origin-Opener-Policy "same-origin"
Header set Cross-Origin-Embedder-Policy "require-corp"Express (Node)
// Basic example
app.use((req, res, next) => {
res.setHeader('Cross-Origin-Opener-Policy', 'same-origin');
res.setHeader('Cross-Origin-Embedder-Policy', 'require-corp');
next();
});Serving a resource that opts into CORP
If a specific resource (e.g., a worker script or image) is on a different origin, that origin needs to send:
Cross-Origin-Resource-Policy: cross-originOr a less permissive value like same-site or same-origin if that fits the hosting arrangement. See MDN: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Resource-Policy
Note: Many public CDNs do not send CORP. If you need those assets with COEP enabled, either host them on your origin, ask the vendor to add CORP, or proxy them through your server/edge layer.
Testing and debugging
- Start with the Report-Only headers. They will produce console reports when a resource would be blocked.
- Open DevTools > Console. The browser will log which resources are blocked and why (CORP missing, cross-origin frame, etc.).
- Use a staging environment. Enabling COEP/COOP on a high-traffic production page without testing often leads to broken analytics or ads.
- If you see failures, check whether the blocked resource can add
Cross-Origin-Resource-Policyor whether you can serve the asset same-origin.
Browsers also provide helpful error messages pointing to missing CORP or failing embedder checks.
Migration checklist - safe sequence to roll out COOP/COEP
- Audit all embedded cross-origin resources: scripts, images, fonts, iframes, workers.
- Enable Report-Only headers and collect reports for a few days:
Cross-Origin-Opener-Policy-Report-OnlyandCross-Origin-Embedder-Policy-Report-Only. - Identify blocked resources and categorize: vendor can add CORP, proxyable, movable to same origin, or incompatible.
- For vendor-hosted resources: ask vendor to add CORP or switch to vendor endpoints that support CORP. If impossible, consider proxying through your server/edge.
- Replace/host critical third-party scripts yourself if licensing and security policy allow it.
- Once blocked items are resolved or mitigated, switch from Report-Only headers to enforced headers.
- Monitor errors and crash/replay telemetry after enforcement.
Compatibility and platforms
- Cross-origin isolation APIs and strict COEP/COOP checks are supported by modern desktop and mobile Chromium-based browsers and recent Firefox versions, but behavior and rollout timing may vary. Always test across the browsers you support.
- Some older browsers simply ignore unknown headers and will not provide cross-origin isolation benefits; design fallbacks accordingly.
- See MDN and the web.dev guide for up-to-date compatibility notes: https://web.dev/coop-coep/ and https://developer.mozilla.org/
Patterns & anti-patterns
Good patterns
- Proxy vendor assets at the edge and add CORP/CSP headers centrally.
- Use
same-origin-allow-popupsif you must open popups and maintain opener comms. - Use Report-Only headers as a discovery phase.
Anti-patterns
- Turning on COEP/COOP in production without auditing third-party resources.
- Assuming CORS solves COEP failures. It does not; CORP is required for COEP’s resource opt-in model.
When to enable cross-origin isolation (short guide)
Enable COOP+COEP when:
- You need SharedArrayBuffer, high-resolution timing APIs, or other features that require cross-origin isolation.
- You are prepared to manage or host third-party resources.
Delay enabling when:
- Your site relies heavily on third-party assets that cannot or will not add CORP headers or be proxied.
Example: enabling SharedArrayBuffer safely
- Audit the page and all subresources. Ensure they will load under COEP.
- Deploy report-only:
Cross-Origin-Embedder-Policy-Report-Only: require-corpandCross-Origin-Opener-Policy-Report-Only: same-origin. - Fix failures (host resources same-origin, add CORP on resource origins, proxy, or remove third-party asset).
- Enforce COEP + COOP headers.
- Use the SharedArrayBuffer API in your scripts. The browser will allow it only when cross-origin isolation is active.
Further reading and references
- MDN: Cross-Origin-Opener-Policy - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Opener-Policy
- MDN: Cross-Origin-Embedder-Policy - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Embedder-Policy
- MDN: Cross-Origin-Resource-Policy - https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Cross-Origin-Resource-Policy
- Google Web Dev: COOP and COEP guide - https://web.dev/coop-coep/
Conclusion - the payoff
COOP and COEP are not just security headers; together they create cross-origin isolation - a foundational platform for safer pages and new, powerful browser APIs. Migration needs planning: start with report-only, audit all resources, and resolve or proxy incompatible assets. Do the work once. Then you get safer interactions, immunity to opener-based tampering, and access to performance and memory APIs that were previously unsafe. That’s worth the effort.