· deepdives · 6 min read
Understanding Portal API: Bridging Your Frontend and Backend like a Pro
Learn what a Portal API is, why it matters, how it fits between frontend and backend, and practical patterns and implementations (REST, GraphQL, gRPC-web, WebSockets) with code examples and best practices for building robust, secure, and performant APIs.
Outcome-first: by the end of this article you’ll be able to design and implement a Portal API that cleanly mediates between your frontend and backend services - improving security, performance, and developer experience.
Why that matters: modern apps have many backend services, multiple frontend clients, and evolving product needs. Without a focused API layer (a “portal”), you end up with duplicated logic, brittle contracts, and hard-to-secure surfaces. This piece walks you through the concept, patterns, implementation examples, and an actionable checklist you can use today.
What is a “Portal API”?
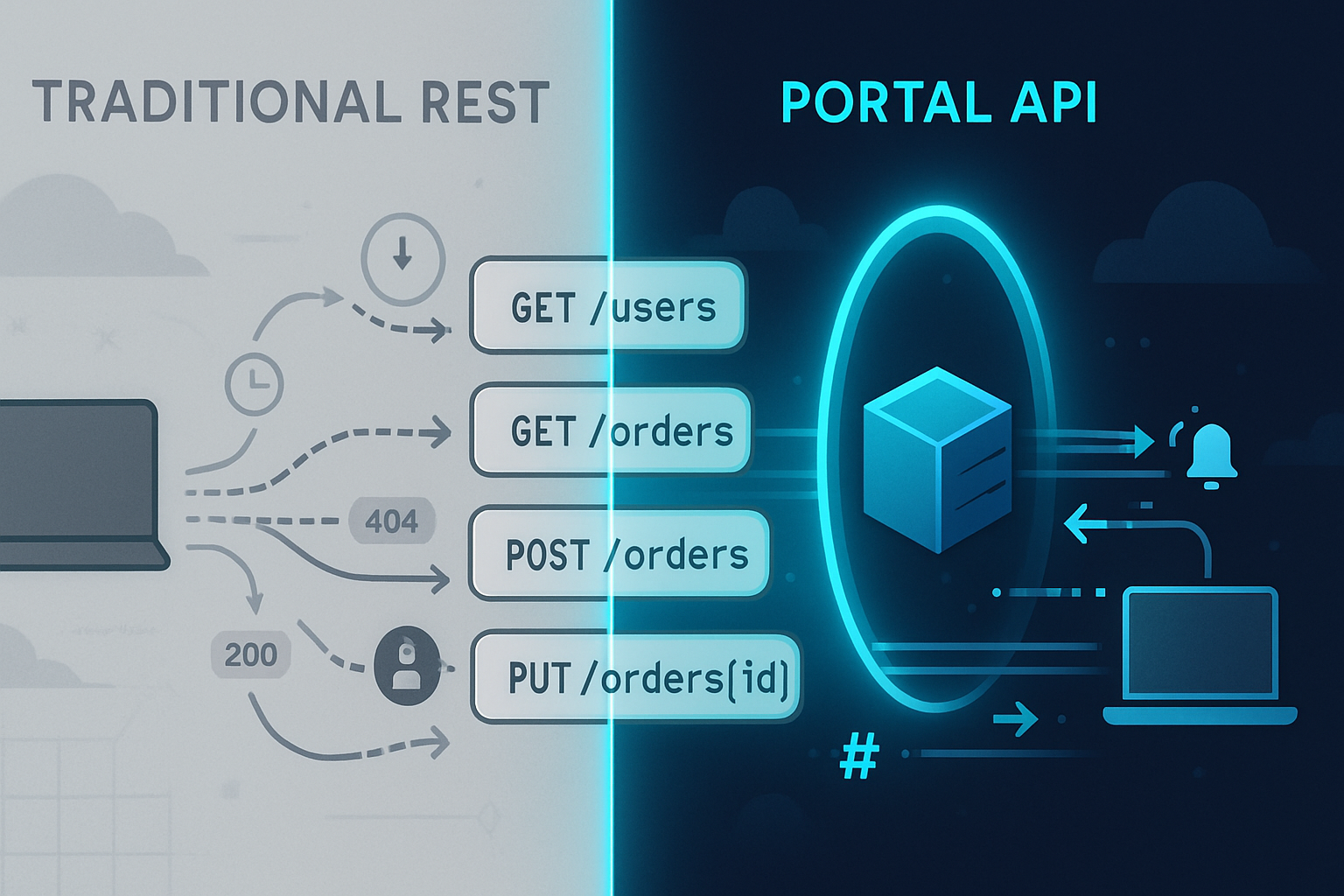
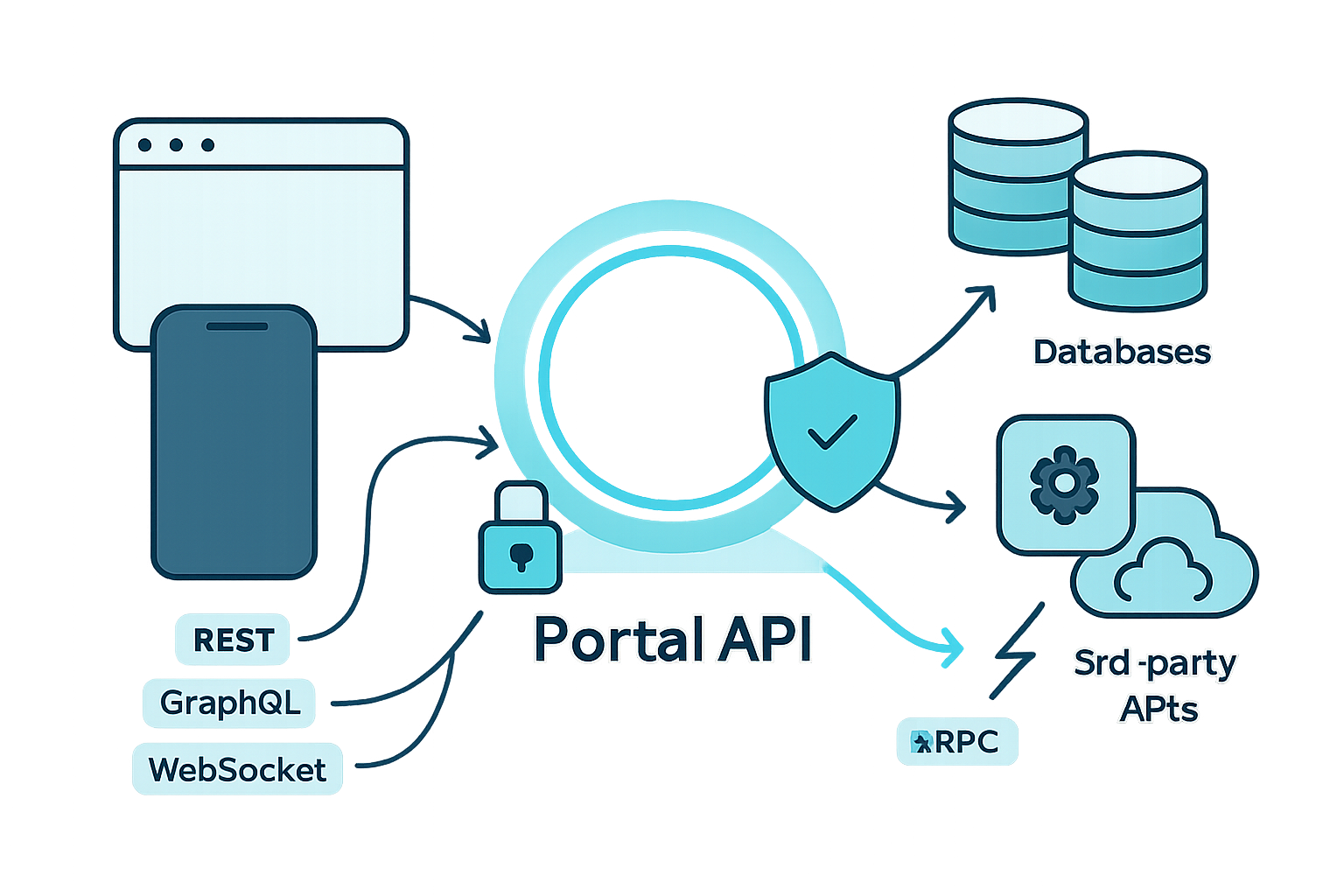
A Portal API is the logical API layer that sits between client apps (web, mobile, embedded) and your backend systems (microservices, databases, third-party APIs). Think of it as a gateway and aggregator that:
- exposes a consistent contract to clients
- enforces security and usage policies
- composes and transforms backend responses
- optimizes data delivery (caching, batching, pagination)
It is not a single technology. It can be implemented as a monolithic gateway, an API gateway (like Kong or AWS API Gateway), or a lightweight server you control with routing and orchestration logic.
Why use a Portal API? - quick benefits
- One surface for authentication, rate-limiting, and logging.
- Reduced coupling: frontends don’t need to know internal service boundaries.
- Better performance: response aggregation, caching, and transport choices.
- Faster iteration: adapt the portal contract while evolving internals.
Simple. Powerful. Necessary for scale.
Core communication patterns
Different apps and use-cases require different transports and schemas. The Portal API can expose any or several of the following:
REST
- Ubiquitous, cache-friendly, straightforward.
- Best for CRUD-style resources.
- Use HTTP verbs, status codes, and conventional URIs.
Example frontend fetch:
// REST fetch from a Portal API
const res = await fetch('/api/users/123', {
headers: { Authorization: 'Bearer ...' },
});
const user = await res.json();GraphQL
- Single endpoint, flexible queries from clients.
- Great when clients need to tailor payload shapes.
- Enables built-in batching and schema introspection.
Example using Apollo Client:
import { ApolloClient, InMemoryCache, gql } from '@apollo/client';
const client = new ApolloClient({
uri: '/graphql',
cache: new InMemoryCache(),
});
const QUERY = gql`
query GetUser($id: ID!) {
user(id: $id) {
id
name
posts {
id
title
}
}
}
`;
const { data } = await client.query({ query: QUERY, variables: { id: '123' } });gRPC-web
- Strongly typed, high-performance, binary transport.
- Useful for internal apps and low-latency scenarios when the frontend supports it.
WebSockets / Server-Sent Events (SSE)
- For real-time updates and push-based communication.
- Portal can multiplex sockets and route messages to appropriate backend services.
Hybrid approach
Many production systems mix these: GraphQL for complex queries, REST for public CRUD endpoints, WebSockets for live updates.
Security, policies, and operational concerns
A Portal API is the natural place to centralize these concerns:
- Authentication & Authorization: OAuth 2.0 / JWTs / API Keys. Validate tokens and map user claims to backend calls.
- Transport security: Always use TLS.
- CORS: Configure explicitly for allowed origins.
- Rate limiting & quotas: Protect your backend from abuse.
- Input validation & schema enforcement: Reject malformed requests early.
- Audit logging and observability: Centralize logs, traces, and metrics.
- Secrets management: Don’t hardcode credentials. Use vaults or environment-based secrets.
References: OAuth2 and JWT patterns at the OAuth 2.0 spec and JWT RFC, and OWASP API Security api-security.
Practical implementation: a minimal Node.js Portal API
Below is a simple example that demonstrates an Express-based portal aggregating two backend services and exposing both REST and WebSocket behavior.
Server (portal) example using Express + http-proxy-middleware + ws:
// portal-server.js (Node.js)
const express = require('express');
const { createProxyMiddleware } = require('http-proxy-middleware');
const http = require('http');
const WebSocket = require('ws');
const app = express();
app.use(express.json());
// Authentication middleware (very simple example)
app.use((req, res, next) => {
const token = req.headers.authorization?.split(' ')[1];
if (!token) return res.status(401).json({ error: 'Missing token' });
// validate token here
req.user = { id: 'user-1' }; // pretend
next();
});
// Proxy to user-service
app.use(
'/api/users',
createProxyMiddleware({ target: 'http://localhost:4001', changeOrigin: true })
);
// Aggregation endpoint that composes data from multiple services
app.get('/api/dashboard', async (req, res) => {
const [usersRes, statsRes] = await Promise.all([
fetch('http://localhost:4001/users').then(r => r.json()),
fetch('http://localhost:4002/stats').then(r => r.json()),
]);
res.json({ users: usersRes, stats: statsRes });
});
const server = http.createServer(app);
const wss = new WebSocket.Server({ server, path: '/ws' });
wss.on('connection', ws => {
ws.send(JSON.stringify({ type: 'welcome', ts: Date.now() }));
// In production, you would authenticate and then route messages to services
});
server.listen(3000, () => console.log('Portal API listening on :3000'));Notes:
- The portal protects and validates requests before forwarding them to internal services.
- Aggregation reduces round trips for the client.
- The WebSocket server can be used to push events to clients.
Frontend usage patterns
- Keep client requests aligned to the portal contract.
- Use caching layers (HTTP cache, SWR, React Query) to avoid redundant API calls.
- Handle authentication centrally: keep token refresh logic in one place.
- For real-time flows, connect to the portal’s socket endpoint rather than to many services.
Example: a React hook using fetch and caching (pseudo):
import useSWR from 'swr';
const fetcher = url =>
fetch(url, { headers: { Authorization: `Bearer ${getToken()}` } }).then(r =>
r.json()
);
export function useDashboard() {
return useSWR('/api/dashboard', fetcher);
}API design considerations
- Versioning: prefer path or header-based versioning (e.g. /v1/ or Accept-Version header). Major changes should bump versions.
- Error design: return structured errors with codes and human messages. Example: { code: ‘USER_NOT_FOUND’, message: ‘User 123 not found’ }.
- Pagination & filtering: standardize on cursor-based pagination for scalability.
- Idempotency: for unsafe operations (POST), support idempotency keys where appropriate.
- Telemetry: emit traces (OpenTelemetry) and metrics for request duration, errors, and throughput.
Performance patterns
- Response caching: use CDN / edge caching for public, cacheable resources.
- Backend caching: portal can cache aggregated responses to reduce load.
- Batching: the portal can batch multiple small requests into one backend call.
- Compression: enable gzip/deflate or Brotli at the portal.
- Connection reuse: use HTTP/2 or keep-alive for backend connections.
When not to centralize everything in the Portal
- Avoid overloading the portal with heavy business logic. Keep it as an orchestrator and policy enforcer.
- For extremely high-throughput internal service-to-service communication, direct calls between services may be more efficient.
- If a client requires very specialized data shapes that only one service knows, consider exposing a lightweight dedicated endpoint.
Real-world patterns and tools
- API gateways: Kong, AWS API Gateway, Azure API Management - they handle auth, throttling, and routing.
- Service meshes: Istio, Linkerd - useful for service-to-service concerns; they complement the portal.
- GraphQL server: Apollo, Hasura - especially helpful when many client types need flexible shapes.
- Reverse proxies & caching: NGINX, Cloudflare Workers, Fastly for edge routing and caching.
Checklist: Building a production-ready Portal API
- Single entrypoint for client traffic (or a controlled set of endpoints).
- AuthN/AuthZ enforced and centralized.
- Rate limits and quotas set.
- Input validation and schema checks.
- Structured error responses and HTTP semantics.
- Observability: logs, metrics, distributed traces.
- Caching strategy documented and implemented.
- Versioning policy established.
- Secrets and credentials correctly stored and rotated.
- Automated tests and contract tests between portal and backend.
Final thoughts
A Portal API is more than a router. It’s the contract between your clients and the complexity of your backend. When designed intentionally it becomes the single place to secure, optimize, and evolve your product’s communication surface. That saves time. It reduces risk. It lets frontend teams move faster without needing deep knowledge of every microservice - and it keeps your architecture maintainable as you scale.
References:
- Fetch API - MDN: https://developer.mozilla.org/en-US/docs/Web/API/Fetch_API
- GraphQL: https://graphql.org/
- gRPC-Web: https://github.com/grpc/grpc-web
- WebSockets - MDN: https://developer.mozilla.org/en-US/docs/Web/API/WebSockets_API
- OWASP API Security: https://owasp.org/www-project-api-security/
- OAuth 2.0: https://datatracker.ietf.org/doc/html/rfc6749