· deepdives · 6 min read
Exploring the Future of IoT: Building a Generic Sensor API
Learn how a Generic Sensor API streamlines IoT device communication - unifying diverse sensors, easing integration, improving security, and enabling scalable edge-to-cloud deployments with practical designs, protocols, and examples.
What you’ll get from this article
A clear, practical path to designing a Generic Sensor API that makes IoT devices speak one language. You’ll learn the core abstractions, recommended protocols and data models, security best practices, and a sample API design you can implement today. Read on and you’ll be able to prototype a flexible, interoperable sensor integration layer for edge and cloud systems.
Why a Generic Sensor API matters - outcome first
IoT projects fail or stall when every device uses a different data format, transport, discovery mechanism, and security model. A well-designed Generic Sensor API removes that friction. It lets developers integrate new sensors in hours instead of weeks. It reduces costly adapter code. It improves security by centralizing auth and validation. And it enables analytics and automation to operate on consistent semantic data rather than vendor-specific noise.
Expect these outcomes:
- Faster sensor onboarding.
- Consistent data models for analytics and dashboards.
- Easier edge-cloud orchestration and offline resilience.
- Better interoperability with third-party tools and standards.
Now let’s build toward that.
Design principles (brief, powerful)
- Single, small set of abstractions. Keep it simple. Sensors, observations, and metadata are usually enough. Avoid bloated models.
- Protocol-agnostic semantics. Separate the data model from transport.
- Extensible but constrained. Provide a core schema and allow typed extensions.
- Security and provenance by design. Authenticate, authorize, and sign or attest data where possible.
- Edge-first. Support local processing and intermittent connectivity.
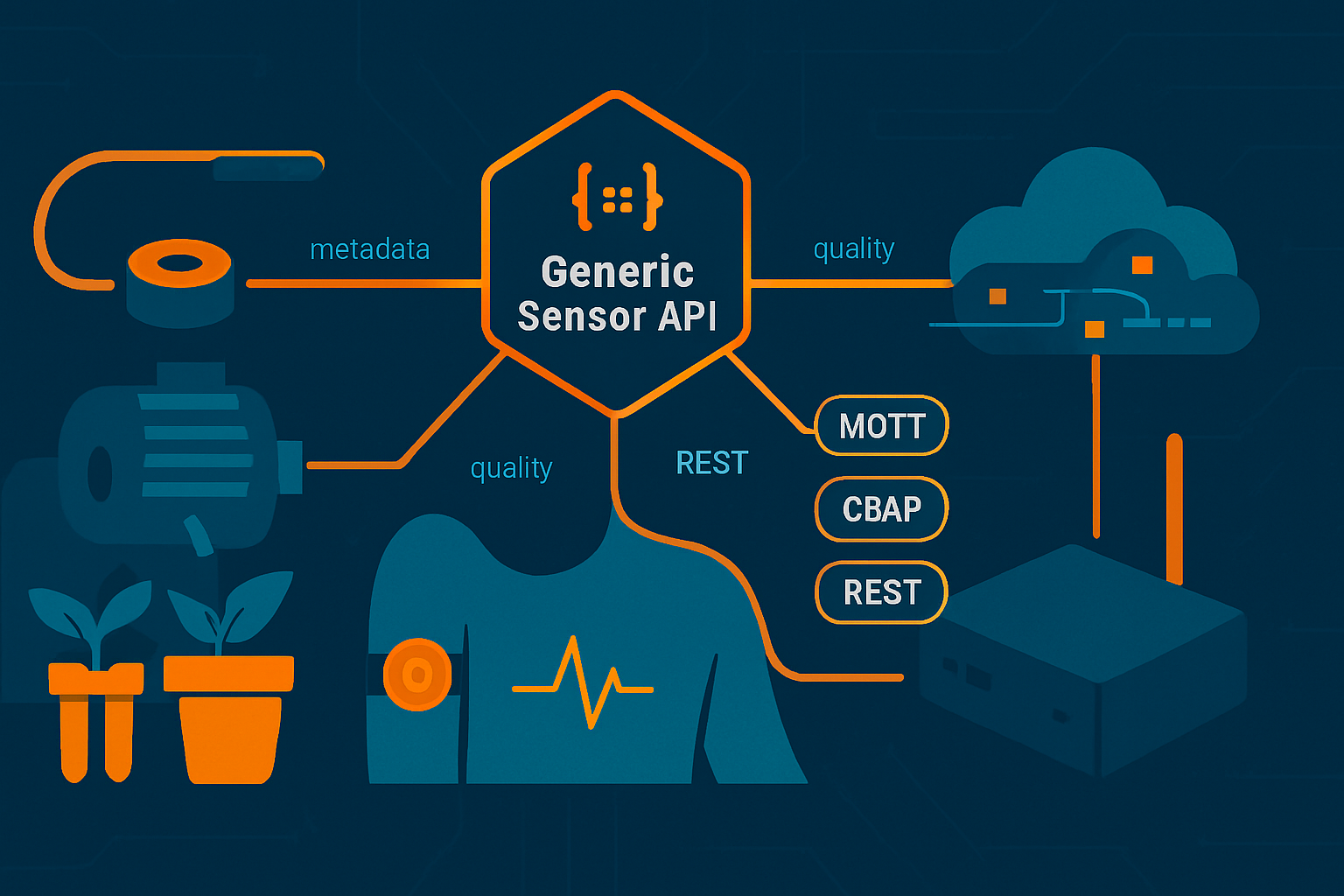
Core abstractions - the API contract
Design the API around three primary concepts:
- Sensor (or Thing): identity and capabilities. Includes id, type, supported observations, metadata (location, model, firmware, owner).
- Observation: a single measured value (or vector) with timestamp and optional quality fields.
- Measurement Schema: the definition of observable properties (units, sampling frequency, data types, ranges).
A minimal JSON representation for these:
{
"sensor": {
"id": "sensor-123",
"type": "temperature",
"model": "Acme-T1000",
"location": { "lat": 37.7749, "lon": -122.4194 }
},
"observation": {
"property": "air_temperature",
"timestamp": "2025-10-25T15:04:05Z",
"value": 22.7,
"unit": "Cel"
}
}This core is intentionally tiny. Implementations can extend with fields like battery, RSSI, status, or calibration metadata.
Data models & formats: what to standardize
Pick a compact, semantically-rich model. Options and trade-offs:
- SenML (IETF): compact, time-series oriented, supported by many constrained devices. Good when minimal overhead matters. SenML
- JSON-LD: adds semantic links and vocabularies. Useful when linking to ontologies and enabling richer queries.
- W3C SensorThings API: higher-level REST model for sensors and observations, integrates well with geospatial data. SensorThings
- CBOR/CBOR-LD: binary, compact, and semantically rich (for constrained devices).
Recommendation: use SenML or SenML+CBOR at the device edge for constrained transports, and convert to a richer JSON-LD or SensorThings model in gateways or cloud for analytics and interoperability.
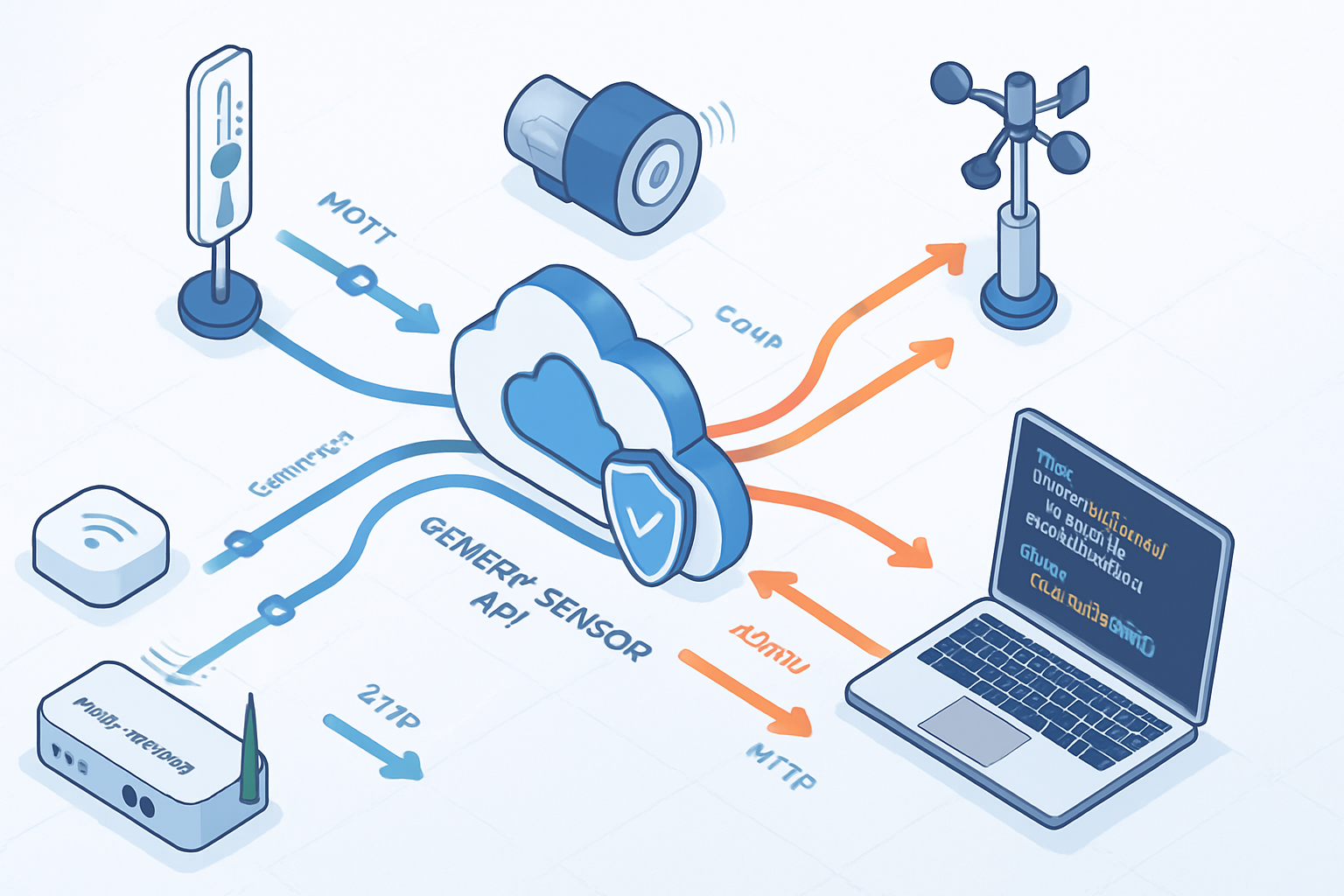
Transport & protocol layer - one API, many transports
Decouple semantics from transport. Support multiple transports but define clear mappings:
- MQTT: lightweight pub/sub, excellent for lossy networks and mobile devices. Use topic conventions and QoS where appropriate. MQTT
- CoAP: restful access for constrained devices with observe support (push). CoAP (RFC 7252)
- HTTP/REST: easy for integration, good for non-constrained devices and management operations.
- WebSockets: useful for real-time dashboards and bidirectional control.
- BLE GATT: for proximity sensors and short-range scenarios.
Define a canonical topic/URI mapping to your sensor abstractions. Example MQTT patterns:
- sensors/
/meta - retained metadata - sensors/
/observations - streaming observations - sensors/
/control - configuration or commands
Use SenML payloads on MQTT for compactness and a server-side translator to the canonical model.
Discovery and registration
Devices must be discoverable. Options:
- Static provisioning for fixed deployments (simple, secure).
- Local discovery (mDNS/SSDP) for plug-and-play in LANs.
- CoAP Resource Directory for constrained environments.
- Cloud registration via device provisioning APIs (e.g., MQTT username/password or SAS tokens).
Include lifecycle states in your model: registered, active, suspended, retired.
Security & privacy (non-negotiable)
Security needs to be baked into every layer:
- Mutual authentication: X.509, Pre-shared keys, or token-based (SAS/JWT) depending on device capability.
- Transport layer encryption: TLS for TCP, DTLS for UDP/CoAP, or secure BLE pairing.
- Fine-grained authorization: topic-based ACLs for MQTT, OAuth scopes for REST.
- Data integrity & provenance: signatures or HMACs for critical telemetry; attest firmware and device identity where possible.
- Privacy controls: minimize PII, support redaction and access controls for location data.
Implement rotation of credentials and a revocation mechanism.
Edge and gateway patterns
Edge computing is essential. Gateways translate transports, perform local aggregation, filtering, and enforce policies.
Common patterns:
- Protocol translation: BLE/Proprietary -> MQTT/CoAP.
- Data normalization: SenML -> canonical JSON-LD.
- Local analytics: anomaly detection, local actuation, reducing cloud cost and latency.
- Caching and store-and-forward: handle intermittent connectivity safely.
Design your Generic Sensor API so that a gateway can fully validate and transform payloads with deterministic mappings.
Interoperability & standards
Adopt or align with existing standards rather than inventing new ones.
- W3C Generic Sensor API (browser-focused) informs abstractions. W3C Generic Sensor API
- OGC SensorThings provides a robust REST model for sensors and observations. OGC SensorThings
- OPC UA for industrial semantic modeling and secure data exchange. OPC Foundation
Mapping strategy: provide adapters to translate between your canonical model and these standards so third-party systems can integrate without heavy custom glue.
Example: a simple REST contract (read/write)
Design a consistent REST surface if you expect HTTP clients:
GET /sensors - list sensors POST /sensors - register sensor (body = Sensor) GET /sensors/{id} - get metadata POST /sensors/{id}/observations - submit observation(s) GET /sensors/{id}/observations?from=…&to=… - query
Observation POST payload (bulk-capable):
{
"sensor_id": "sensor-123",
"observations": [
{ "property": "temp", "t": "2025-10-25T15:00:00Z", "v": 22.5, "u": "Cel" },
{ "property": "temp", "t": "2025-10-25T15:05:00Z", "v": 22.7, "u": "Cel" }
]
}Map this to SenML on constrained transports and to SensorThings/JSON-LD in the cloud for richer semantics.
Operational concerns: performance, reliability, observability
- Quality-of-Service: use MQTT QoS levels judiciously. Persist critical observations.
- Batching and compression: reduce overhead on constrained links.
- Rate limiting and back-pressure: protect cloud ingestion pipelines.
- Monitoring: expose metrics on device connectivity, message latency, and error rates.
- Logging and tracing: include correlation IDs for observations to trace from device to analytics.
Migration strategy for existing deployments
- Define canonical model and mapping rules.
- Build or configure a gateway that performs translation and security enforcement.
- Incrementally onboard sensors by registering them with minimal metadata.
- Replace or refactor device-side clients gradually; favor over-the-air updates.
- Monitor and tighten policies after rollout.
This incremental approach avoids big-bang rewrites while reaping early benefits.
Example: MQTT flow (concise pseudocode)
Device publishes SenML array to sensors/sensor-123/observations (retained = false). Gateway subscribes, validates, enriches with location metadata, and forwards to cloud API.
Pseudocode:
on mqtt_message(topic, payload):
if topic matches sensors/+/observations:
senml = parse(payload)
if validate(senml):
canonical = translate_to_canonical(senml)
add_provenance(canonical)
post_to_cloud('/sensors/{id}/observations', canonical)Where the field is headed - trends to watch
- Semantic interoperability: more JSON-LD and ontology-driven sensor models.
- Binary semantic formats: CBOR-LD to shrink overhead while preserving meaning.
- Secure hardware-backed identity: TPM/secure elements becoming standard in industrial sensors.
- Edge ML: models running on gateways to reduce data volumes and enable fast actions.
A Generic Sensor API that embraces these trends will remain useful and future-proof.
Conclusion - the payoff
A small, well-defined Generic Sensor API yields outsized benefits: faster integration, stronger security, easier analytics, and lower operational cost. Build a compact core set of abstractions, separate semantics from transport, and provide robust gateway patterns. Do that and your next IoT rollout will be faster, cheaper, and more secure.
References
- W3C Generic Sensor API: https://www.w3.org/TR/generic-sensor/
- OGC SensorThings API: https://www.ogc.org/standards/sensorthings
- SenML (IETF RFC 8428): https://tools.ietf.org/html/rfc8428
- MQTT: http://mqtt.org
- CoAP (RFC 7252): https://tools.ietf.org/html/rfc7252
- OPC UA (OPC Foundation): https://opcfoundation.org