· deepdives · 6 min read
The Controversy of Privacy: Shape Detection API in Surveillance and Its Ethical Implications
A deep look at how the Shape Detection API can be used - and abused - for surveillance, the ethical problems that follow, real-world regulatory touchpoints, and practical technical and policy mitigations for developers and lawmakers.

Outcome first: by the end of this article you will be able to explain how the Shape Detection API can become a surveillance multiplier, identify concrete ethical harms, and recommend technical and policy controls that meaningfully reduce risk.
Why this matters - fast
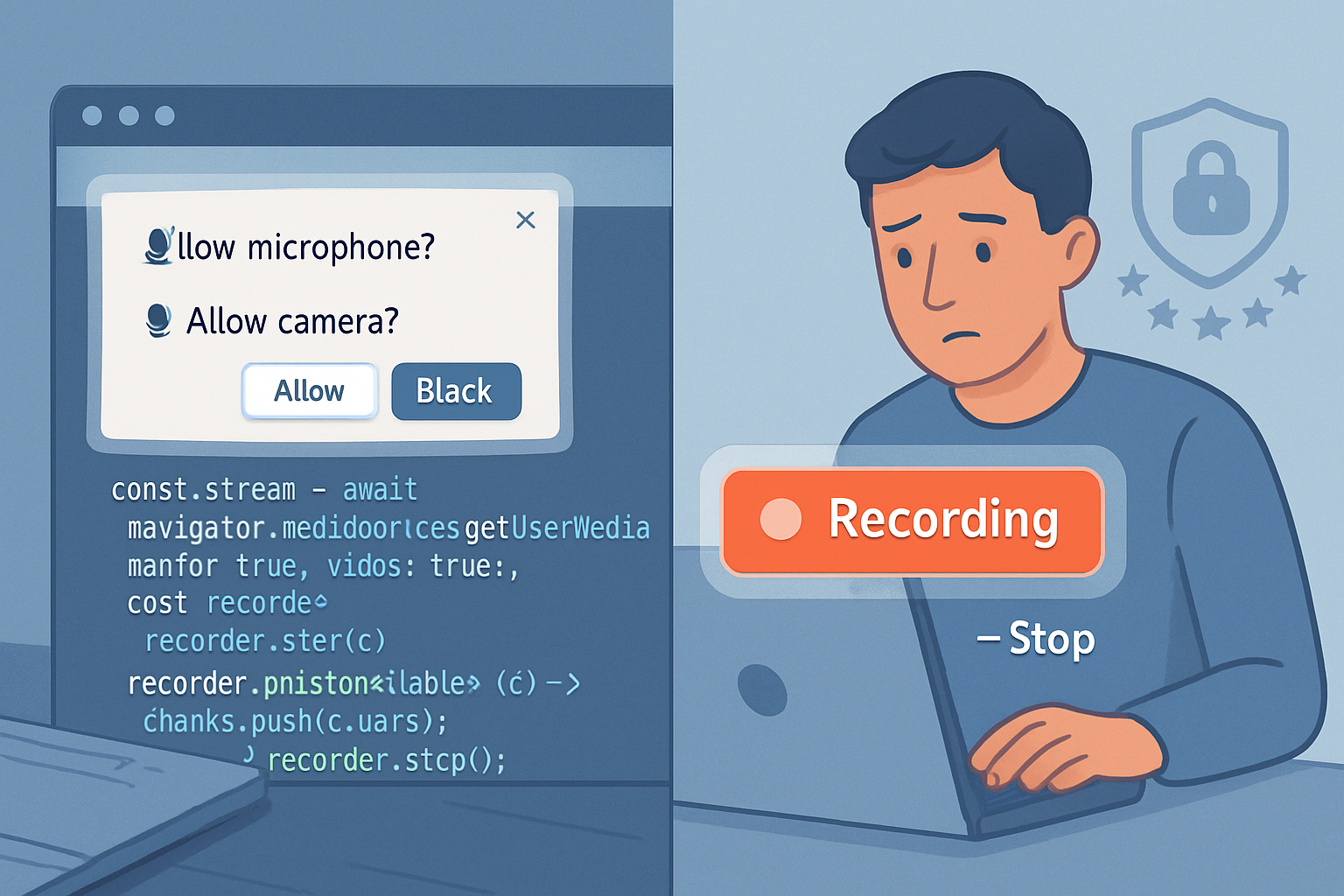
The Shape Detection API makes it trivial for web pages and apps to detect faces, barcodes, and shapes in images and video. That convenience is powerful. It also lowers the barrier to mass surveillance. Small code changes can scale to city-wide tracking. That is the risk. You need to know how, and what to do about it.
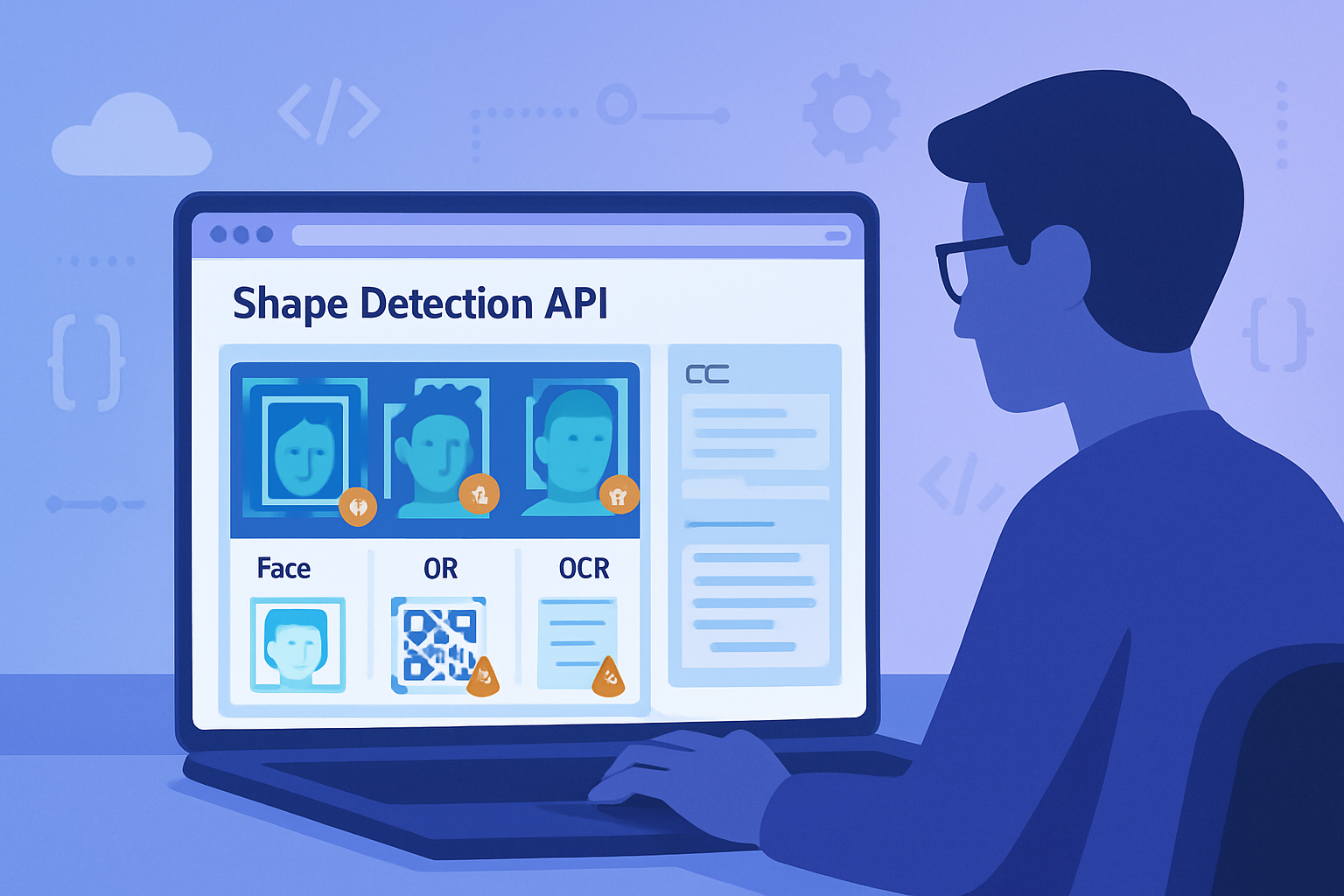
What is the Shape Detection API? (briefly)
The Shape Detection API is a browser-facing interface that provides programmatic access to detectors such as FaceDetector and BarcodeDetector for images and live video streams. Implementations and specs are documented by browser vendors and community groups; a readable overview is on MDN: https://developer.mozilla.org/en-US/docs/Web/API/Shape_Detection_API and the spec work is available from the W3C/community repositories: https://w3c.github.io/shape-detection/.
A typical usage pattern looks like this (simplified):
const detector = new FaceDetector();
const faces = await detector.detect(videoFrame);
// faces -> bounding boxes, landmarks, maybe confidenceNote: the API does detection (locating faces/barcodes/shapes). It does not by itself provide identity (“who is this”), but detection is the essential first step for tracking, re-identification, and automated targeting.
How detection becomes surveillance - the technical path
- Detection -> Tracking: bounding boxes across frames form trajectories. That lets systems follow a person through multiple cameras or sessions.
- Detection + Re-identification: combine detections with face-embedding models or identifiers (login, payment info) to link physical presence to identity.
- Detection + Metadata: timestamps, location, and behavioral signals (how long someone looked at a shelf, who they met) create rich profiles.
- Scale: a single script using the API can run on many pages or devices, aggregating data centrally.
A capability that appears innocuous locally becomes a surveillance network when combined with tracking, model-based re-identification, and centralized logging.
Ethical harms to watch for
- Loss of anonymity in public spaces: detection plus tracking erodes the natural anonymity people expect in public.
- Function creep: detection tools meant for accessibility or UX testing can be repurposed for profiling, dating apps scraping, targeted harassment, or discriminatory policing.
- Discriminatory impact: face detection and downstream recognition models have documented accuracy disparities across demographics, increasing the risk of wrongful identification and disparate enforcement.
- Consent illusion: users often do not know detection is happening, or cannot meaningfully opt out when detection runs in the background of common web pages.
- Chilling effects: awareness of pervasive detection changes public behavior, limiting freedom of expression and association.
Privacy and legal touchpoints
GDPR (EU): biometric data used for unique identification is a special category of personal data requiring explicit legal bases and strict safeguards. See an overview at the European Commission: https://ec.europa.eu/info/law/law-topic/data-protection_en and the GDPR text: https://gdpr-info.eu/.
BIPA (Illinois): biometric identifiers and templates have special protections and consent rules under the Biometric Information Privacy Act. That law has enabled high-profile litigation against companies collecting biometric data without adequate notice and consent. See: https://www.ilga.gov/legislation/ilcs/ilcs3.asp?ActID=3004.
Municipal and national restrictions: several cities and jurisdictions worldwide have restricted or banned law-enforcement or municipal use of facial recognition systems in public spaces. The EU’s proposed AI Act also recognizes high-risk biometric ID systems and proposes stricter governance: https://digital-strategy.ec.europa.eu/en/policies/european-approach-artificial-intelligence.
Note: legal regimes differ. This article does not constitute legal advice. Use it as a policy and technical primer.
The gray area: when detection is legitimate
Not all uses are harmful. Examples of legitimate uses include:
- Accessibility features (helping visually impaired users understand scenes).
- Payment confirmations that remain fully opt-in and on-device.
- Barcode/QR scanning for product access or check-in flows.
- Privacy-preserving analytics where only aggregate counts (no identifiers) are stored.
The ethical difference often lies in consent, data minimization, transparency, and the feasibility of re-identification.
Practical mitigations for developers (technical controls)
- Require explicit, granular, context-specific consent before enabling detectors.
- Prefer on-device processing. Keep raw images and detections local when feasible; avoid cloud uploads unless strictly necessary.
- Enforce purpose limitations in code and server policies. Log and audit what detectors are used and why.
- Minimize outputs: return only what the UX needs (e.g., a single boolean for face-present rather than full landmark arrays), and avoid persistent unique identifiers.
- Rate-limit and throttle detection to impede mass scraping or covert continuous surveillance.
- Provide visible indicators when camera or detection features are active (clear UI elements and persistent permission settings).
- Implement retention limits and secure deletion for any detection metadata collected.
- Apply differential privacy or aggregation when reporting analytics so individuals cannot be re-identified from published statistics.
Example of minimizing output:
// Instead of returning full bounding boxes to the server,
// return only a boolean that a face is present, computed on-device.
const hasFace = (await detector.detect(frame)).length > 0;
reportToServer({ hasFace }); // minimal telemetryOrganizational and product governance
- Data Protection Impact Assessments (DPIAs): perform DPIAs before deploying detection systems, and update them as capabilities evolve.
- Transparency and user controls: publish clear, human-readable explanations of detection features and provide simple opt-out flows.
- Independent audits: bring in third-party audits and publish redacted results or summaries.
- Design reviews: include ethicists, legal counsel, and civil-society perspectives in product reviews.
Regulatory recommendations (what lawmakers and regulators should consider)
- Permission model: require explicit, informed consent for online face detection and biometric processing, with clear revocation paths.
- Restrict sensitive use cases: ban or tightly regulate government and law-enforcement access without warrant and oversight.
- Certification and accountability: require vendors and platforms that enable biometric detection at scale to undergo certification for privacy and fairness.
- Transparency mandates: require entities using detection systems to publish transparency reports, impact assessments, and complaint mechanisms.
- Data minimization and retention rules: set strict limits on what may be stored and for how long, with regular deletion enforced by design.
- Liability and consumer remedies: provide clear legal remedies for misuse and erroneous identification.
Many of these measures echo existing laws (GDPR, BIPA) and the approaches now being debated in the EU AI Act.
Anticipating counterarguments
- Innovation slowdown: critics say strict rules will stifle useful features. The counter: thoughtful regulation and privacy-by-design spur trust and sustainable adoption.
- Technical workarounds: some claim bad actors will move to native apps or models to bypass web API restrictions. True - but layered policy (regulation, platform controls, civil-society monitoring) raises the cost of misuse.
A practical checklist before you ship detection features
- Have you performed a DPIA? Yes/no.
- Is the feature strictly necessary for the user-facing purpose? Yes/no.
- Is processing done on-device? If not, why?
- Do you collect identifiers or persistent metadata? If yes, can you avoid it?
- Do you have a clear, revocable consent flow and visible indicator when detection runs?
- Is there an auditable log and a retention/deletion schedule?
- Have you evaluated disparate impact across demographic groups?
If you cannot answer these with confidence, pause development and redesign for privacy.
Final thoughts - the strongest point
Detection is not just code. It is power: the power to observe, to link, to influence, and to exclude. The Shape Detection API lowers the engineering barriers to that power. That creates opportunity - and responsibility. Without strong design defaults, transparent governance, and enforceable regulation, what starts as useful functionality will become a surveillance multiplier. We must insist that privacy, agency, and democratic oversight travel with every line of detection code we publish.