· tips · 6 min read
The Art of Obfuscation: Protecting Your JavaScript Code from Prying Eyes
A practical, in-depth guide to JavaScript obfuscation: what it does, when to use it, common techniques (minification, mangling, control-flow flattening, string encryption), tool examples, build integration, limitations, and best practices.

Why obfuscate JavaScript?
Shipping JavaScript to the browser means delivering readable source to users. Obfuscation makes that source harder to understand, reverse-engineer, or pirate. Typical goals are:
- Increase the effort required to analyze or copy proprietary algorithms.
- Reduce casual tampering and script kiddie attacks.
- Discourage straightforward reuse of business logic.
Important caveat: obfuscation is not a security boundary. It raises the cost for an attacker but doesn’t prevent motivated reverse engineers. Think of obfuscation as a speed bump, not a locked vault. See Security through obscurity for context.
Common techniques
Below are the most-used techniques, from gentle to aggressive.
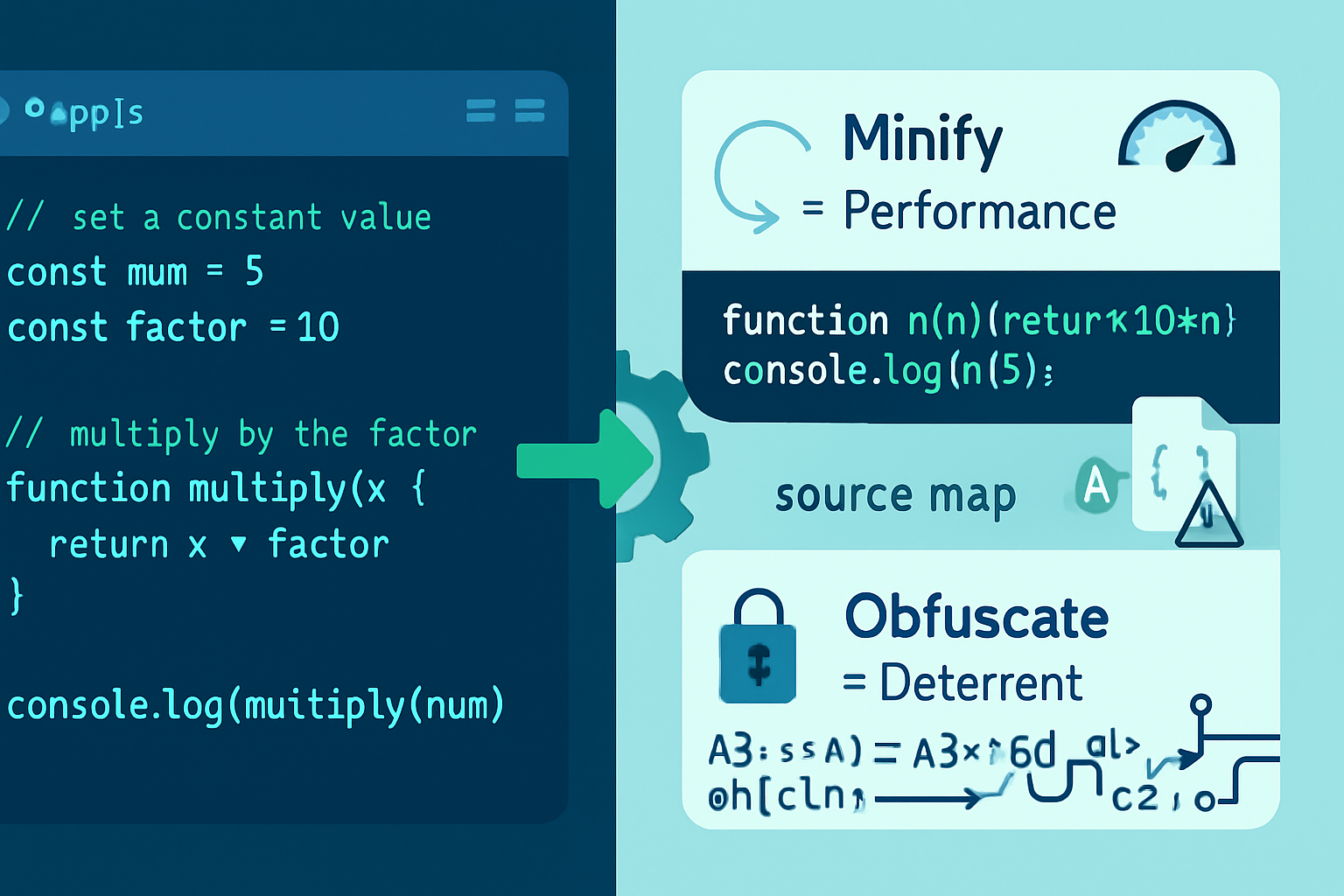
1) Minification
Minification removes whitespace, comments and can shorten some identifiers to reduce size. It improves load times and offers modest obfuscation.
Tools: Terser, UglifyJS, Google Closure Compiler.
Example with Terser (CLI):
# install
npm install -g terser
# minify
terser src/app.js -o dist/app.min.js --compress --mangleBefore:
function greet(name) {
// greet the user
console.log('Hello ' + name);
}After (minified + mangled):
function a(b) {
console.log('Hello ' + b);
}Minification is low-cost and generally recommended for production builds.
2) Mangling / Identifier renaming
Mangler replaces variable/function names with short names (a, b, c). This makes the code harder to read but preserves functionality. Most minifiers include mangling.
Terser example (node API):
const terser = require('terser');
const result = terser.minify(code, { mangle: true, compress: true });3) Control-flow flattening
Transforms code into a less-structured control flow (switch/while state machines). This significantly increases analysis cost but also increases bundle size and runtime overhead.
Tools: javascript-obfuscator supports control-flow flattening.
4) String encryption / string array
Detects literal strings and encrypts or stores them in encoded arrays, replacing usages with runtime decoders. Protects API keys, messages, or constants from easy reading.
5) Dead code injection / junk code
Inserts non-functional or misleading code paths to confuse static analysis. Useful against pattern-based scanners but increases bundle size and may impact performance.
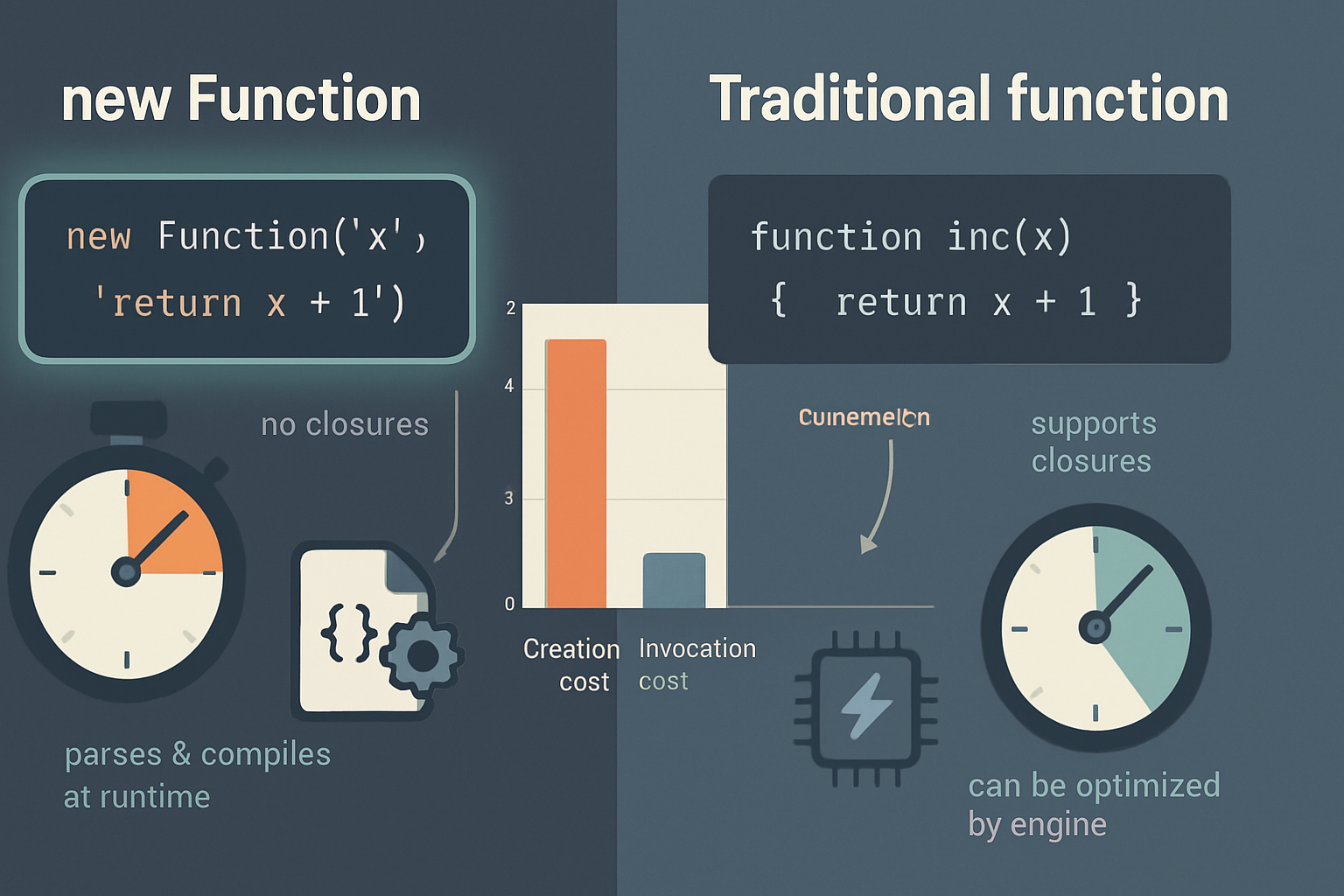
6) Eval / runtime decryption / virtualization
Wraps code pieces in runtime decoders or virtual machines implemented in JS. Extremely obfuscated but also slow and sometimes trigger security policies (CSP forbids eval by default). Consider only for small, extremely sensitive sections.
Tools and examples
javascript-obfuscator (open-source)
A widely-used JS obfuscator with many options: control-flow flattening, string array, rotate string array, string array encoding, dead code injection, domain locking, and more.
Install:
npm install -g javascript-obfuscatorCLI example:
javascript-obfuscator dist/app.js --output dist/app.obf.js --compact true \
--control-flow-flattening true --control-flow-flattening-threshold 0.75 \
--string-array true --string-array-encoding base64Node API example:
const JavaScriptObfuscator = require('javascript-obfuscator');
const obfuscated = JavaScriptObfuscator.obfuscate(
`function greet(name){console.log('Hello '+name);}`,
{
compact: true,
controlFlowFlattening: true,
controlFlowFlatteningThreshold: 0.75,
stringArray: true,
stringArrayEncoding: ['base64'],
rotateStringArray: true,
}
).getObfuscatedCode();
console.log(obfuscated);javascript-obfuscator is effective and configurable, but it increases file size and CPU work on load.
Project: https://github.com/javascript-obfuscator/javascript-obfuscator
Google Closure Compiler
Can do advanced optimizations (including property renaming and cross-file optimizations) when code is annotated correctly with goog or type information. Excellent for aggressive size/rename work but requires careful code structure.
Docs: https://developers.google.com/closure/compiler
Commercial solutions (e.g., Jscrambler)
If you need stronger protections, commercial products like Jscrambler offer anti-tampering, domain-locking, constant freezing, and a large set of obfuscation transforms with enterprise support. These typically provide better guardrails and integrations but cost money.
Bundler integrations
- Webpack plugin: webpack-obfuscator
- Use Terser via terser-webpack-plugin
Webpack example (webpack.config.js snippet):
const JavaScriptObfuscator = require('webpack-obfuscator');
module.exports = {
// ... other config
plugins: [
new JavaScriptObfuscator(
{
rotateStringArray: true,
controlFlowFlattening: true,
},
['excluded_bundle.js']
),
],
};Practical examples and pitfalls
Example: protecting a small algorithm
Original:
export function calculateScore(user, actions) {
let score = 0;
for (const a of actions) {
score += a.weight * (user.level + 1);
}
return score;
}A combination of mangling + control flow flattening + string array will turn this into something legal but hard to follow. However, keep in mind:
- Performance: control-flow transformations and runtime decoders add CPU work.
- Debuggability: stack traces will be unreadable without source maps.
Source maps - the double-edged sword
Source maps let you debug obfuscated/minified code by mapping back to original sources. But if you publish source maps publicly, you effectively release your original code.
Best practice:
- Keep source maps out of public CDN. Upload them only to error tracking services that require them (e.g., Sentry) and restrict access.
- In CI, generate source maps and store them in a secure artifact store for debugging.
CSP and eval
Many obfuscation techniques rely on eval or new Function. If your site uses a strict Content Security Policy (CSP) without unsafe-eval, those approaches will fail. Prefer transforms that don’t rely on eval when you must respect CSP.
Limitations: what obfuscation won’t do
- Prevent code theft by a motivated attacker (they can always run and study the code, or attach a debugger).
- Prevent API misuse when the backend accepts client-side calls - protect servers with authentication, rate limiting, and server-side validation.
- Fix insecure algorithms or secrets. Never embed private keys or long-term secrets in client code.
For highly sensitive logic, move it server-side or into a native+WASM module with proper licensing checks.
Alternatives and complements
- Move critical logic to the server (best security).
- Use WebAssembly (WASM) to make reverse engineering harder (not impossible) - see MDN WebAssembly.
- Licensing and code-signing to enforce usage terms.
- Monitoring and tamper detection (detect modified clients and report back).
Performance and compatibility checklist
- Measure: benchmark obfuscated vs non-obfuscated bundles in realistic devices.
- Test: ensure CSP, ad blockers, or security extensions don’t break your obfuscated runtime.
- Source maps: keep them private and upload to error tracking services if needed.
- Build pipeline: integrate obfuscation as a final step in CI after minification and bundling.
Legal and ethical considerations
- Respect third-party code licenses - some open-source licenses do not permit certain types of distribution without attribution.
- Disclose obfuscation choices in privacy/security docs if it affects user consent or debuggability.
- Don’t use obfuscation to hide malicious behavior. Transparency with users and customers remains important.
Practical CI/CD pattern
- Build -> bundle -> minify (Terser) -> run tests.
- Obfuscate only production artifacts (javascript-obfuscator or commercial tool) as a final step.
- Generate source maps but store them in a restricted location and upload to your error monitoring tool.
- Deploy obfuscated code to CDN.
Quick start checklist
- Use minification and mangling by default (Terser/Uglify).
- Apply stronger obfuscation for particularly sensitive modules only.
- Avoid embedding secrets in client code.
- Keep source maps private and integrate with your error-tracking.
- Measure performance and test across target devices.
Conclusion
Obfuscation is a valuable tool for raising the bar against casual inspection and copying of JavaScript. Used wisely, it complements other security practices such as server-side enforcement, proper authentication, and licensing. Choose the right level of obfuscation for your threat model: lightweight minification for performance and modest concealment, or advanced transforms where the extra risk and latency are justified.
References
- Terser: https://github.com/terser/terser
- javascript-obfuscator: https://github.com/javascript-obfuscator/javascript-obfuscator
- Google Closure Compiler: https://developers.google.com/closure/compiler
- Jscrambler: https://jscrambler.com/
- Webpack: https://webpack.js.org/
- MDN - Use a source map: https://developer.mozilla.org/en-US/docs/Tools/Debugger/How_to/Use_a_source_map
- MDN - WebAssembly overview: https://developer.mozilla.org/en-US/docs/WebAssembly
- Security through obscurity: https://en.wikipedia.org/wiki/Security_through_obscurity