· tips · 6 min read
Obfuscation vs. Minification: Understanding the Real Differences and Use Cases
A practical guide explaining what JavaScript minification and obfuscation do, how they differ, when to use each, security implications, tooling, and best-practice checklist for safe build pipelines.
Introduction - what you’ll get out of this article
You will finish this article clear about when to minify, when to obfuscate, and when neither is appropriate. You’ll know the real benefits and limits of each technique, how they affect performance, debugging, and security, and you’ll get a practical checklist to apply them correctly in your build pipeline.
Why this matters. Because mixing up the two can cost you performance, developer time, or-worse-give you a false sense of security.
Definitions: quick and concrete
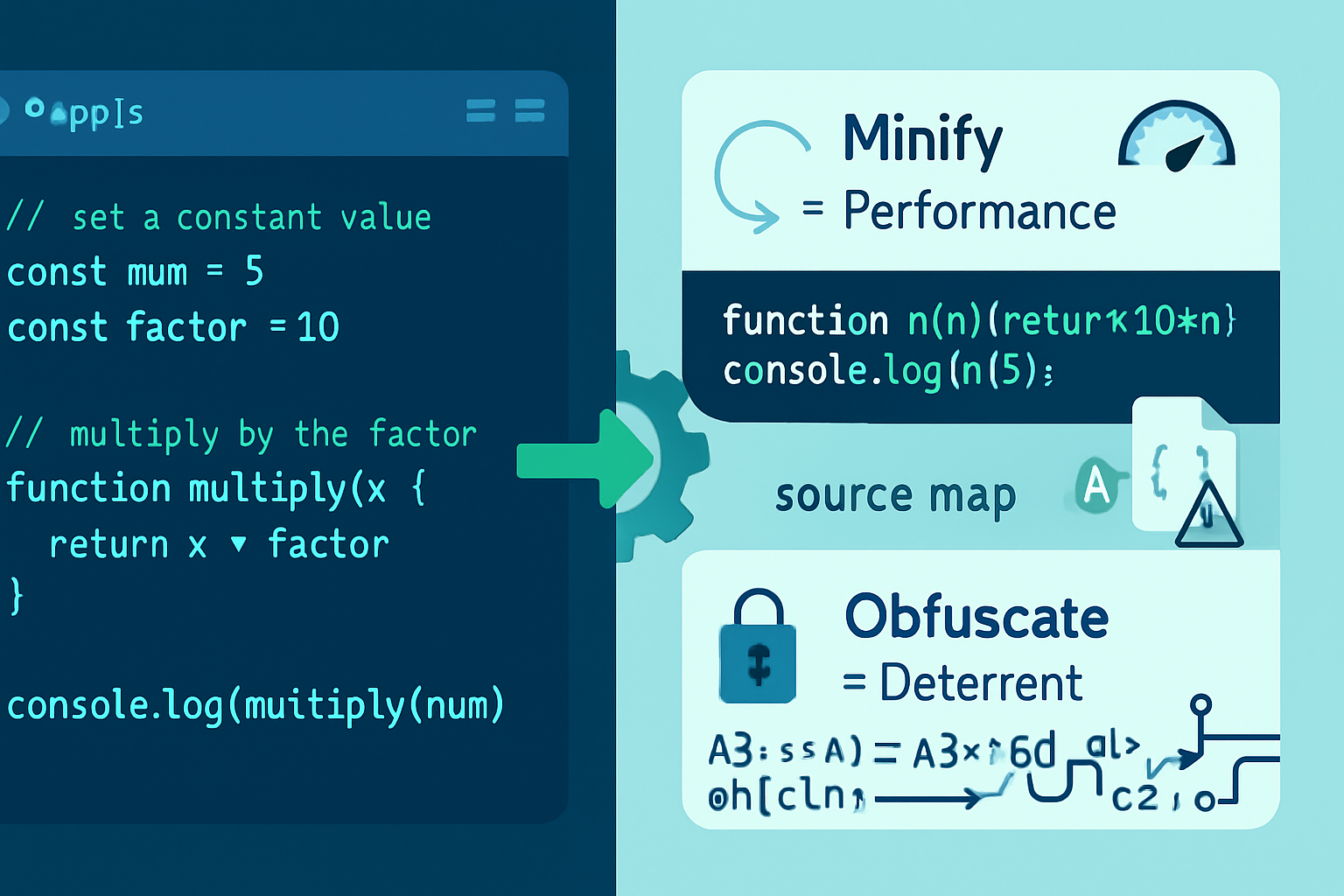
- Minification: a build step that removes unnecessary characters (whitespace, comments) and shortens identifiers where safe, to reduce file size and improve network/parse performance. Tools: Terser, UglifyJS.
- Obfuscation: a transformation that intentionally makes code harder to read and understand by changing names, control flow, and adding layers of indirection. Tools: javascript-obfuscator, commercial engines.
Minification optimizes for bytes. Obfuscation optimizes for human comprehension (makes it harder to reverse-engineer).
How each works (high level)
Minification techniques
- Whitespace and comment removal.
- Shortening local variable and function names when scope allows.
- Dead-code elimination and tree-shaking (often handled by bundlers/compilers before minification).
- Simple syntactic rewrites to reduce token count.
Obfuscation techniques
- Renaming identifiers globally or aggressively (including export names in some modes).
- String encoding (Base64, hex, or custom schemes) and runtime decoding.
- Control-flow flattening: rewriting straight-line code into convoluted branches and jump tables.
- Inserting fake/unused code and opaque predicates that make static analysis noisy.
- Wrapper functions, eval or Function() usage for dynamic evaluation.
A key difference: minification is designed to be semantics-preserving and unobtrusive; obfuscation often changes structure drastically while attempting to preserve runtime behavior.
Goals and tradeoffs
Minification
- Primary goal: smaller download size and faster parse/execution.
- Secondary benefit: a small degree of obscurity (very short names make scanning slightly harder).
- Tradeoffs: minimal - some source maps are needed to preserve debug quality.
Obfuscation
- Primary goal: raise the cost for someone trying to understand or reuse your code.
- Secondary effects: usually increases execution time (CPU cost) and bundle size (runtime decoders, extra code).
- Tradeoffs: harder debugging, brittle builds, potential legal/ethical issues if applied to third-party code, and only deterrence - not real protection for secrets.
When to use which (practical rules)
Use minification in nearly every production frontend build.
- It reduces bandwidth and improves performance. No debate.
- Keep source maps in private artifact storage or use controlled access in production monitoring.
Consider obfuscation only when you need a modest deterrent against casual inspection and you accept costs.
- Example use cases: protecting proprietary client-side algorithms that must run in the browser (rare); raising the bar against script kiddies or casual copying.
- Don’t use it to protect secrets (api keys, credentials, algorithms that, if secret, should run on server-side).
Avoid obfuscation when the code is performance-sensitive, heavily debugged in production, or legally required to be auditable (open-source, regulated environments).
Security implications and common misconceptions
Myth: “Obfuscation makes my app secure.”
Fact: Obfuscation is a deterrent, not defense. Determined attackers can reverse-engineer obfuscated JavaScript using deobfuscators, dynamic analysis, and runtime instrumentation. See Snyk’s analysis: “Obfuscation is not security”.
Key security pitfalls
- Secrets in client code are exposed. Any secret embedded in client-side code (API keys, crypto keys) can be extracted at runtime regardless of obfuscation. Treat the client as an untrusted environment.
- Source maps can leak original code. If you publish source maps accidentally, you’ve undone both minification and obfuscation. Read how source maps work and how they can leak source: MDN - Source maps.
- Obfuscation can mask vulnerabilities. If you obfuscate before a security or license audit, reviewers may miss issues. Obfuscation is incompatible with transparent compliance processes.
- False confidence in IP protection. Obfuscation slows down an adversary but will not stop a motivated reverse engineer (especially when combined with native tooling and runtime hooking).
Tooling and concrete examples
Minification with Terser (common in modern builds)
- Example command (installed via npm):
npx terser dist/app.js -c -m -o dist/app.min.js- Typical config: compression (-c), mangling (-m) shortens local names but leaves global APIs intact unless you explicitly enable reserved or module scope transforms.
Obfuscation with javascript-obfuscator
- Example command (installed via npm):
npx javascript-obfuscator dist/app.js --output dist/app.obf.js --compact true --control-flow-flattening true --string-array true- Options to consider:
- control-flow-flattening: makes analysis harder but costs CPU and size.
- string-array & rotate/string-array-encoding: hide string literals but add runtime decoders.
Notes on mixing both
- Minify first, obfuscate the minified output if you must obfuscate. Minifying after obfuscation can break the obfuscator’s assumptions or remove protective wrappers.
- Some obfuscators include a minification step; inspect outputs carefully and measure size/perf.
Source maps: friend and foe
- Source maps restore readable debugging. Use them in dev and private monitoring only.
- Never accidentally publish production source maps to the public CDN. That exposes your original sources.
- If you obfuscate, you can generate source maps but store them securely (e.g., private S3 buckets, CI artifacts) linked only to authorized teams and error-tracking tools.
Performance considerations
- Minification generally reduces parse and download time.
- Obfuscation can increase CPU usage at runtime because of decoders, added indirection, and complex control flow. Run benchmarks on representative devices (especially low-end mobile).
- Measure: bundle size, first contentful paint (FCP), Time to Interactive (TTI), and CPU usage on target devices.
Developer experience and debugging
- Minification + source maps: good UX. You can debug production with symbols mapped back to originals (if maps are available to you).
- Obfuscation: painful debugging. Stack traces are often useless without trusted mapping and you risk leaking mapping if you store it carelessly.
- Recommendation: maintain a reproducible build pipeline so you can map any deployed artifact back to sources when needed.
Legal, licensing, and ethical notes
- If you distribute third-party open-source code and obfuscate it, check license terms (some licenses require keeping notices). Obfuscation may break compliance.
- For code that must be auditable (healthcare, finance, security products), obfuscation may be inappropriate.
Practical checklist before you obfuscate
- Ask: Why am I obfuscating? Is server-side execution an option instead?
- Ensure you are not hiding secrets client-side.
- Measure baseline performance and bundle size before applying obfuscation.
- Build reproducibly and store build artifacts and source maps in private storage.
- Run security scans and audits on original source (not the obfuscated bundle).
- Validate license obligations for bundled/third-party code.
- Test on target devices for performance impact.
- Document the process for future maintainers (how to reproduce, where maps live, who can access them).
Example scenarios - quick decisions
- Single-page app wanting faster load times: Minify (always). Do not obfuscate unless you have a clear, measured need.
- Browser-only proprietary algorithm you don’t want copied: Consider obfuscation but weigh cost vs. moving logic server-side.
- Widget distributed to customers for embedding on their sites: Avoid obfuscation if clients may need to debug or audit the widget; minify instead.
Final recommendations
- Treat minification as a standard step in your build pipeline. It is safe, effective, and aligned with performance best practices.
- Treat obfuscation as a specialized tool - a deterrent with costs. Use it sparingly and never as a substitute for server-side security.
- Protect source maps and build artifacts. Source maps are valuable for debugging - and dangerous if leaked.
Conclusion
Minification optimizes; obfuscation confuses. Use minification for performance; consider obfuscation only when you accept reduced debuggability, increased runtime cost, and the reality that it only delays a determined reverse engineer. Do not rely on obfuscation to protect secrets. Obfuscation is a cost, not a bulletproof shield.