· deepdives · 7 min read
Understanding WebRTC Security: Protecting Your Real-Time Communications
A deep dive into WebRTC security: how it protects media, common vulnerabilities (IP leaks, signaling risks, misconfigured TURN), encryption techniques (DTLS, SRTP), and practical hardening recommendations for developers and ops teams.
Why WebRTC security matters
WebRTC enables real-time audio, video, and data directly between browsers and native apps without plugins. That convenience brings new attack surfaces: media streams, peer discovery, signaling channels, and infrastructure (STUN/TURN). Understanding how WebRTC secures media and where it can fail is essential for building safe, privacy-respecting communication apps.
Key foundational resources:
- The WebRTC spec and high-level docs: https://www.w3.org/TR/webrtc/
- WebRTC security overview from the official project: https://webrtc.org/security/
- Developer reference (MDN): https://developer.mozilla.org/en-US/docs/Web/API/WebRTC_API
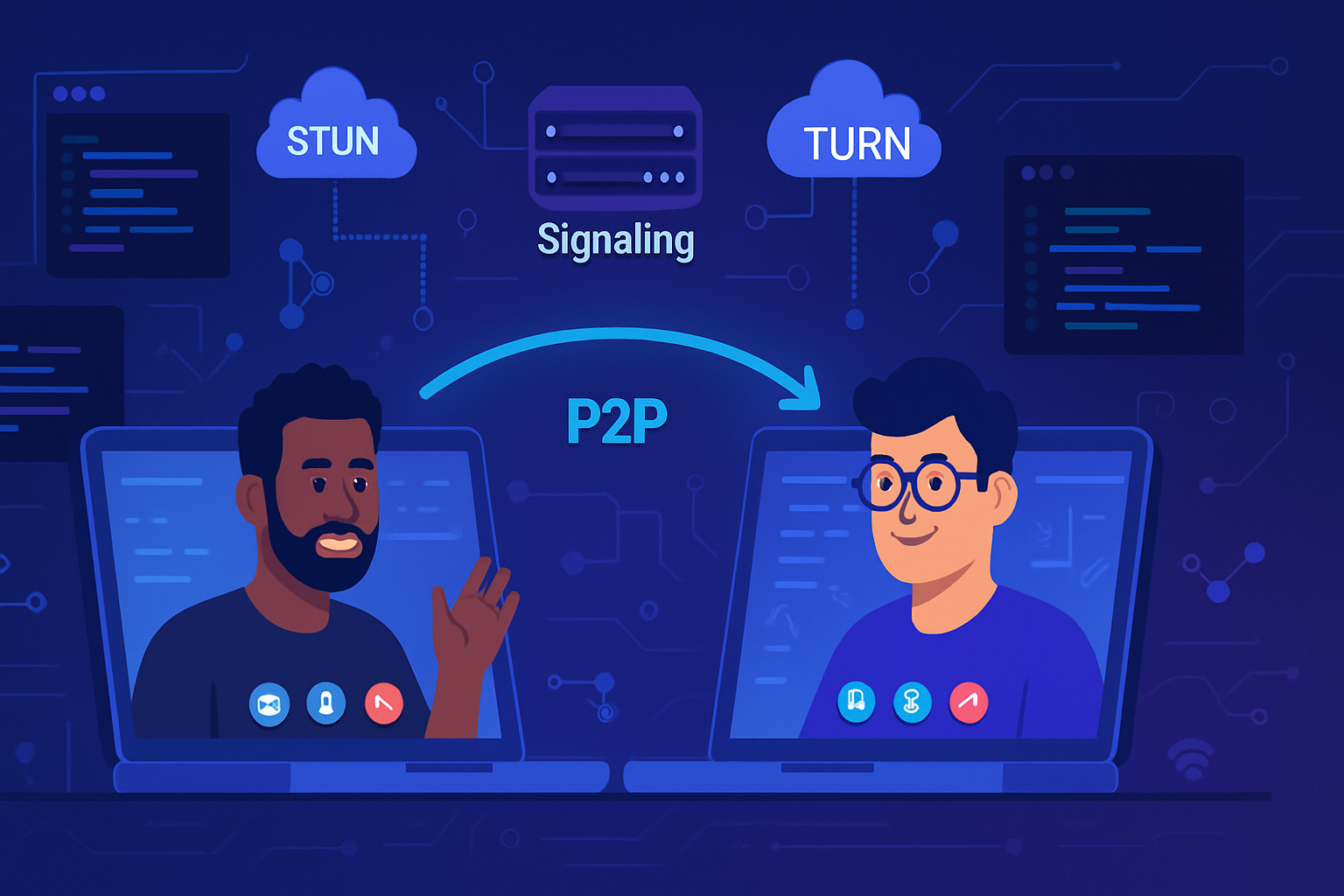
Brief primer: how WebRTC establishes connections (security-relevant pieces)
WebRTC uses several protocols jointly to build real-time connections. The main pieces to keep in mind:
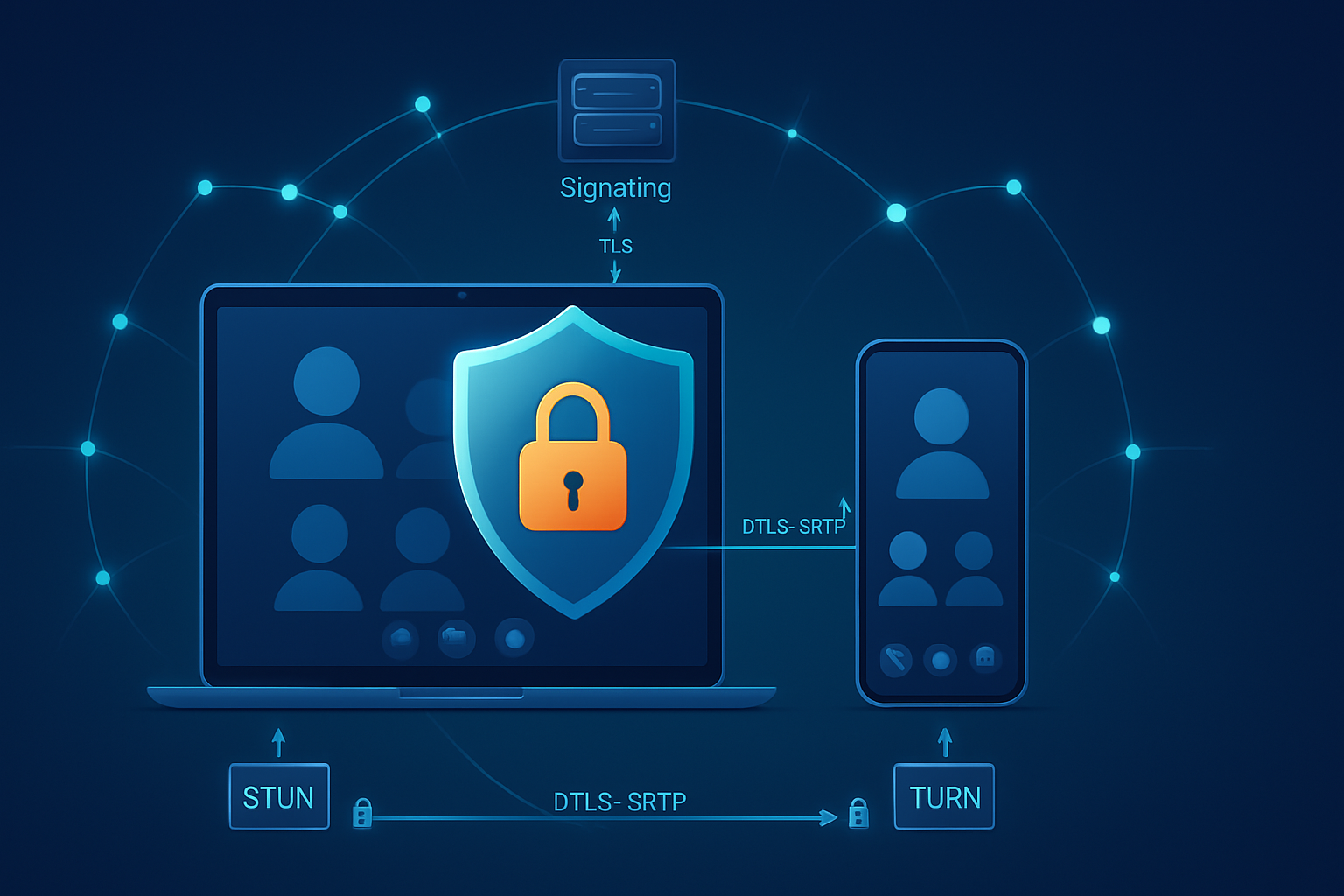
- Signaling: application-specific channel (not defined by WebRTC) used to exchange SDP offers/answers and ICE candidates. This channel must be secured by the application (TLS, authentication).
- ICE (Interactive Connectivity Establishment): finds a path between peers using local, STUN, and TURN candidates. See RFC 8445: https://datatracker.ietf.org/doc/html/rfc8445
- STUN/TURN: STUN discovers public-facing IPs; TURN relays media when direct peer-to-peer fails (STUN: RFC 5389 https://datatracker.ietf.org/doc/html/rfc5389, TURN: RFC 5766 https://datatracker.ietf.org/doc/html/rfc5766).
- DTLS and SRTP: media encryption and integrity are provided by DTLS to negotiate SRTP keys (SRTP: RFC 3711 https://datatracker.ietf.org/doc/html/rfc3711, DTLS: RFC 6347 https://datatracker.ietf.org/doc/html/rfc6347).
WebRTC’s default data and media channels are encrypted (DTLS + SRTP) - but “encrypted by default” does not eliminate all security or privacy risks.
Common vulnerabilities and privacy risks
- IP address leakage (local/private IPs)
- Problem: STUN/ICE discovery can expose a user’s local (private) and public IP addresses to remote peers. Attackers can use this to deanonymize users or fingerprint networks.
- Real-world note: this problem was highlighted early in WebRTC’s deployment; see the Electronic Frontier Foundation’s write-up: https://www.eff.org/deeplinks/2015/04/lets-stop-web-rtc-leaking-users-private-ip-addresses
- Mitigation: modern browsers use mDNS for local candidates (obfuscating local IPs). Where available, ensure you rely on browser defaults, and provide options for users to disable local candidate exposure. You can also prefer ICE policy
relayto force TURN relaying (see configuration example below), though that incurs extra latency and cost.
- Insecure signaling channels
- Problem: Signaling is outside WebRTC and frequently implemented via WebSocket/HTTP. If signaling is sent over plain HTTP/WSS without authentication, attackers can create/join sessions, replay offers/answers, or perform man-in-the-middle attacks.
- Mitigation: Always use TLS (WSS), authenticate and authorize every signaling request (short-lived tokens, OAuth/JWT), validate incoming SDP and candidate payloads, and employ CSRF/XSS protections on the web app.
- Misconfigured or exposed TURN servers
- Problem: Public or poorly configured TURN servers can be abused (relay malicious traffic, act as free bandwidth, or degrade privacy if they log media), and may expose your infrastructure to resource exhaustion.
- Mitigation: Require authentication for TURN, prefer short-lived credentials or REST-based ephemeral credentials, limit CORS/origins, rate-limit allocations and monitor usage.
- Browser and stack vulnerabilities
- Problem: WebRTC implementations in browsers or libraries can have memory corruption, sandbox escapes, or logic bugs allowing eavesdropping or DoS.
- Real-world note: WebRTC-related CVEs have been disclosed; for example, CVE entries for browser engines are tracked in public vulnerability databases (example NVD entry): https://nvd.nist.gov/
- Mitigation: Keep browsers and native WebRTC stacks up to date, adopt secure CI/CD for native components, and subscribe to security advisories for Chromium/Firefox/Apple.
- Server-side issues: signaling servers, recording/archiving, and SFUs
- Problem: Centralized media servers (Mixers/SFUs) can access unencrypted media, and misconfigured storage/recording endpoints can leak media.
- Mitigation: Treat SFUs and recorders as high-sensitivity components; apply strict access control, encrypt media at rest, and, if end-to-end confidentiality is required, explore end-to-end encryption approaches (see below).
- Application-layer attacks (XSS, CSRF, injection)
- Problem: Because WebRTC apps run in browsers and exchange JSON/SDP, they inherit typical web vulnerabilities. Compromised web pages can leak tokens, hijack sessions, or manipulate SDP to subvert features.
- Mitigation: Follow web security best practices: CSP, sanitization, secure cookies, same-site attributes, Content Security Policy, and input validation.
Encryption and confidentiality - what WebRTC gives you
- Mandatory encryption for media and data channels: DTLS negotiates keys for SRTP so media is encrypted in transit. This prevents passive eavesdropping on the network if the attacker cannot access endpoints/TURN servers.
- Authenticity/integrity: DTLS ensures media is received from a peer that established the DTLS handshake.
Limitations:
- End-to-end encryption (E2EE) is not guaranteed for multi-party architectures that use SFUs. SFUs typically decrypt, process (e.g., mix or forward) and re-encrypt media streams. That means SFU operators could access plaintext media unless an E2EE scheme is used.
- Browser and server endpoints are still trust boundaries - if an endpoint is compromised, media can be accessed there.
E2EE options:
- Insertable Streams / client-side encryption: modern browsers expose hooks to process encoded media frames before they are handed off to the WebRTC pipeline. Apps can encrypt media payloads end-to-end. See platform docs and proposals on “insertable streams” (search WebRTC insertable streams for the latest implementations).
- Application-level encryption: encrypting audio/video payloads at the application layer before giving them to WebRTC; typically expensive and complex for real-time.
Practical hardening checklist (developer + ops)
Signaling and application logic
- Use TLS/WSS for signaling and all control APIs.
- Authenticate and authorize every signaling request; use short-lived tokens and refresh flows.
- Validate SDP and candidate messages on the server; reject malformed or unexpected payloads.
- Implement role-based access (hosts vs. guests) and do not rely solely on obscured URLs.
ICE/STUN/TURN
- Prefer ephemeral TURN credentials (short TTL) rather than long-lived static credentials.
- Configure TURN to require authentication and limit allocation time and bandwidth per allocation.
- If privacy is critical, consider
iceTransportPolicy: 'relay'to force TURN relaying (trade-off: latency/cost). - Monitor and alert on unusual TURN usage patterns.
Browser and media hardening
- Keep browser and WebRTC libraries up to date.
- Limit getUserMedia permissions scope (request only needed tracks and sample rates).
- Use browser features to reduce IP exposure (mDNS/local candidate obfuscation) when appropriate.
- Minimize local candidate exposure via configuration and inform users about privacy tradeoffs.
Server hardening and operations
- Treat SFUs/recorders as high-risk components: encrypt media at rest and limit access to operators.
- Log and audit signaling and TURN access; store only necessary logs and purge PII.
- Rate-limit connection attempts and implement anomaly detection (sudden spikes, many short-lived sessions, replayed offers).
User experience and privacy
- Ask for permissions with clear user intent and explain why camera/microphone are needed.
- Show clear UI indicators for active camera/microphone and for remote participant presence.
Example: forcing TURN (in JavaScript)
// Force all ICE candidates to use TURN (relay) only
const pc = new RTCPeerConnection({
iceTransportPolicy: 'relay',
});Note: iceTransportPolicy: 'relay' ensures peers attempt relay paths only. Use carefully - this will route media through your TURN infrastructure and increase costs.
Incident-level examples and lessons
- IP leaks and privacy exposure
- Early WebRTC deployments exposed local IP addresses via STUN, which could deanonymize VPN users. The community responded by adding mDNS candidate obfuscation and browser-side mitigations. (EFF write-up: https://www.eff.org/deeplinks/2015/04/lets-stop-web-rtc-leaking-users-private-ip-addresses)
Lesson: coordinate with browser defaults and inform users about privacy tradeoffs. Regularly review browser tracker behavior and configuration options.
- Browser/WebRTC CVEs
- Like any complex native code, browser WebRTC stacks have received security patches for memory corruption and logic bugs. Keep clients and libraries up to date and subscribe to vendor advisories. Public vulnerability databases (e.g., NVD) and browser security pages list relevant CVEs.
Lesson: patch management is critical. For enterprise deployments, have a fast update path for both client and server components.
- Misconfigured TURN and infrastructure abuse (operational risk)
- Operators who expose unauthenticated TURN services risk bandwidth theft, logging of media, and service disruption. Use authentication and ephemeral credentials; monitor usage.
Lesson: infrastructure configuration is as important as code. Treat TURN servers as first-class security components.
Detection, monitoring, and incident response
- Instrument signaling and TURN servers with metrics and logs (connection counts, auth failures, allocation sizes).
- Alert on anomalies: spikes in TURN relay usage, many failed authentication attempts, unusual geolocation patterns.
- Keep recording/archival controls auditable: who started/stopped recordings and where they are stored.
- Have a documented incident response process: rotate keys/credentials, block offending IPs, notify affected users where applicable.
Designing for security by default: practical recommendations
- Default to secure browser and server configurations; make the secure path the easiest path.
- Prefer ephemeral secrets (TURN credentials, session tokens) and short TTLs.
- Put least privilege into APIs: a client should only be able to act on sessions/devices it owns.
- Limit data retention: log minimally, store recordings only when explicitly required, and encrypt them.
- Provide transparency to users: display participants, show when a session is being recorded, and provide simple privacy controls.
Further reading and references
- WebRTC specification (W3C): https://www.w3.org/TR/webrtc/
- WebRTC security overview: https://webrtc.org/security/
- MDN WebRTC API docs: https://developer.mozilla.org/en-US/docs/Web/API/WebRTC_API
- STUN: RFC 5389 - https://datatracker.ietf.org/doc/html/rfc5389
- TURN: RFC 5766 - https://datatracker.ietf.org/doc/html/rfc5766
- ICE: RFC 8445 - https://datatracker.ietf.org/doc/html/rfc8445
- SRTP: RFC 3711 - https://datatracker.ietf.org/doc/html/rfc3711
- DTLS: RFC 6347 - https://datatracker.ietf.org/doc/html/rfc6347
- EFF on WebRTC IP leakage: https://www.eff.org/deeplinks/2015/04/lets-stop-web-rtc-leaking-users-private-ip-addresses
- OWASP general web application guidance: https://owasp.org/
- National Vulnerability Database (search for WebRTC/Chromium CVEs): https://nvd.nist.gov/
Closing thoughts
WebRTC provides strong transport-level protections out of the box (DTLS/SRTP) but does not remove the need for careful application, infrastructure, and operational security. The main risks are often not the media channel itself but surrounding systems: signaling, TURN infrastructure, browser vulnerabilities, and application-layer logic. Design with the assumption that servers and endpoints can be targeted, minimize the attack surface, and apply defense in depth: secure signaling, authenticated TURN, patched clients/servers, monitoring, and, where required, end-to-end encryption.